Week3
This week we were given a network dump in the form of a PCAP file.
There were 13 challenge questions this week.
To be able to analyze this PCAP file we needed to use a program called Wireshark.
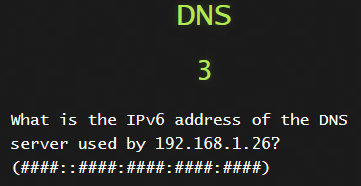
1) DNS
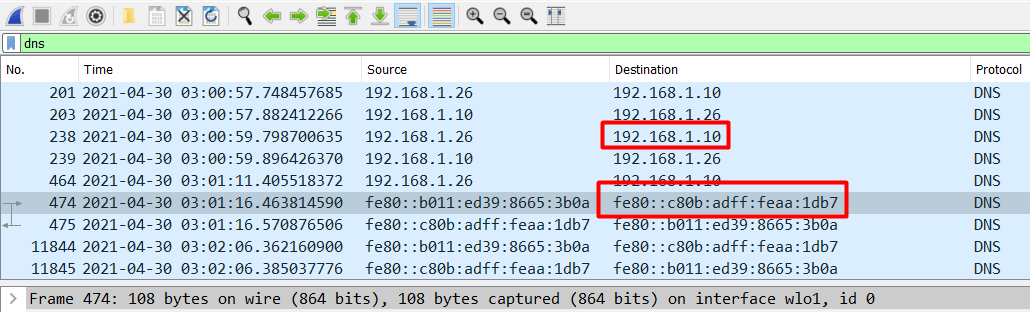
Let’s run a search query for dns in the search bar.
We could also use the query
1
udp.port == 53
We see that 192.168.1.26 is making DNS queries to 192.168.1.10.
We can assume that fe80::b011:ed39:8665:3b0a is 192.168.1.26 and that the other IPv6 address is 192.168.1.10.
2) MAC Address
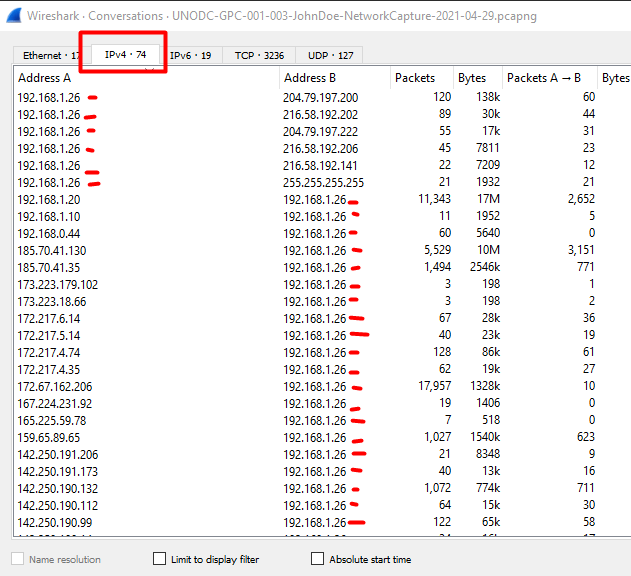
Let’s have a look at what IP Address comes up the most and that will probably be our suspect IP.
On the toolbar at the top click Stastistics and then Conversations.
Click on the IPv4 tab and as you can see, there is one IP that comes up.
If I had to scroll down even more down it would show many more of the same IP.
3) Packets
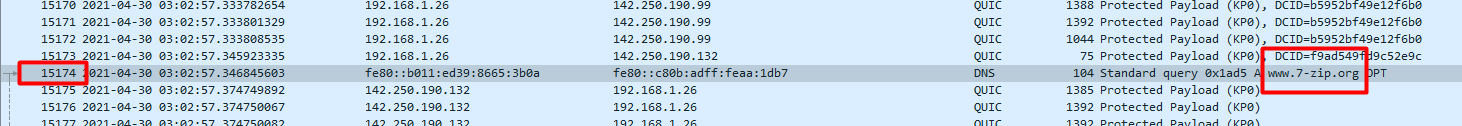
For this we can go directly to the packet ID.
On your keyboard press ctrl + g or on the toolbar</b> click Go and select Go to packet
You will now see on the top right hand side the following.

Enter the packet ID into the field and click Go to packet and we will see the domain name.
4) Passwords!
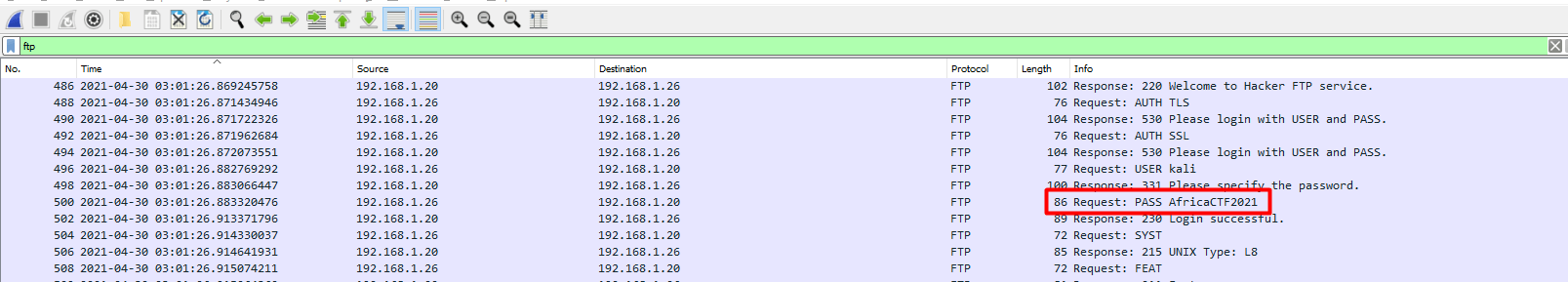
In the search bar, search for ftp and on the rightmost column we can find the password.
5) UDP Data
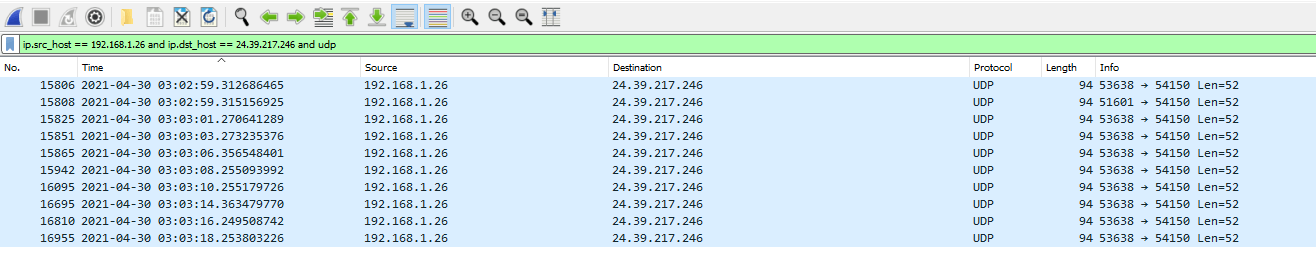
We can craft the following search term to get the result and count them.
1
ip.src_host == 192.168.1.26 and ip.dst_host == 24.39.217.246 and udp
6) Domains
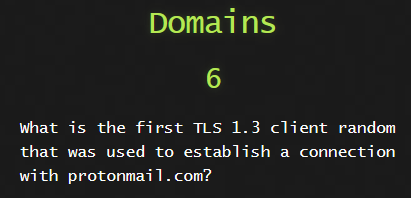
For this one we need to see the TLS Client Hello packets and see what domains they were communicting with.
We can do this by running the following search
1
ssl.handshake.type == 1
We now have to go through each packet and manually check and eventually we find it.
7) Image data
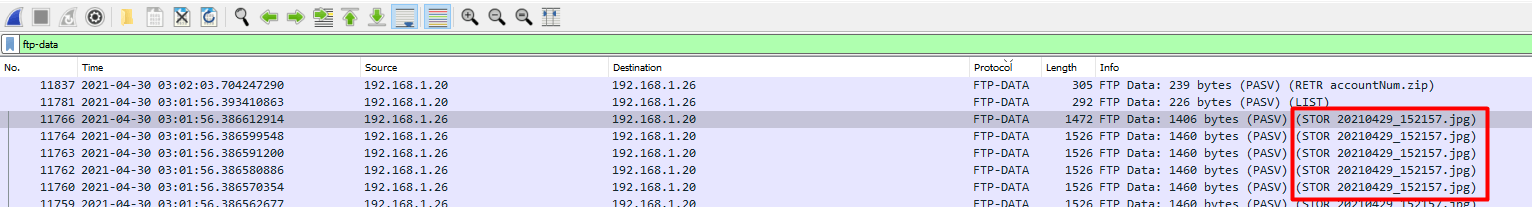
The challenge question mentioned a .jpg so my first thought was to see if it was downloaded with FTP.
I searched for ftp-data and found the following
We can right click on highlighted packet in the above, select Follow and then select TCP Stream or alternativley you can press Ctrl+Alt+Shift+T
We can see in the stream the created date.
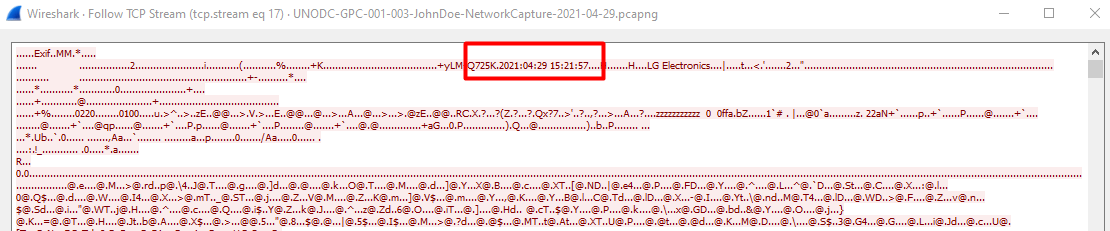
To be honest, we cannot confirm if this IS the created date.
Let us download this image to our local machine.
At the bottom of the TCP Stream window, change the Show data as to Raw and then click Save as… as 202104_29_152157.jpg
Now we can use the exiftool from week 1 to look at the metadata.
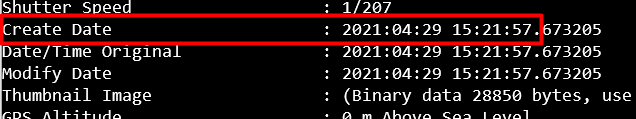
Or if we look at the filename of the .jpg image it has the date taken but one cannot assume that is the created time.
8) Public keys
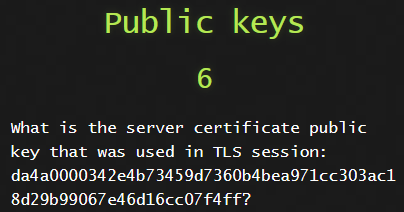
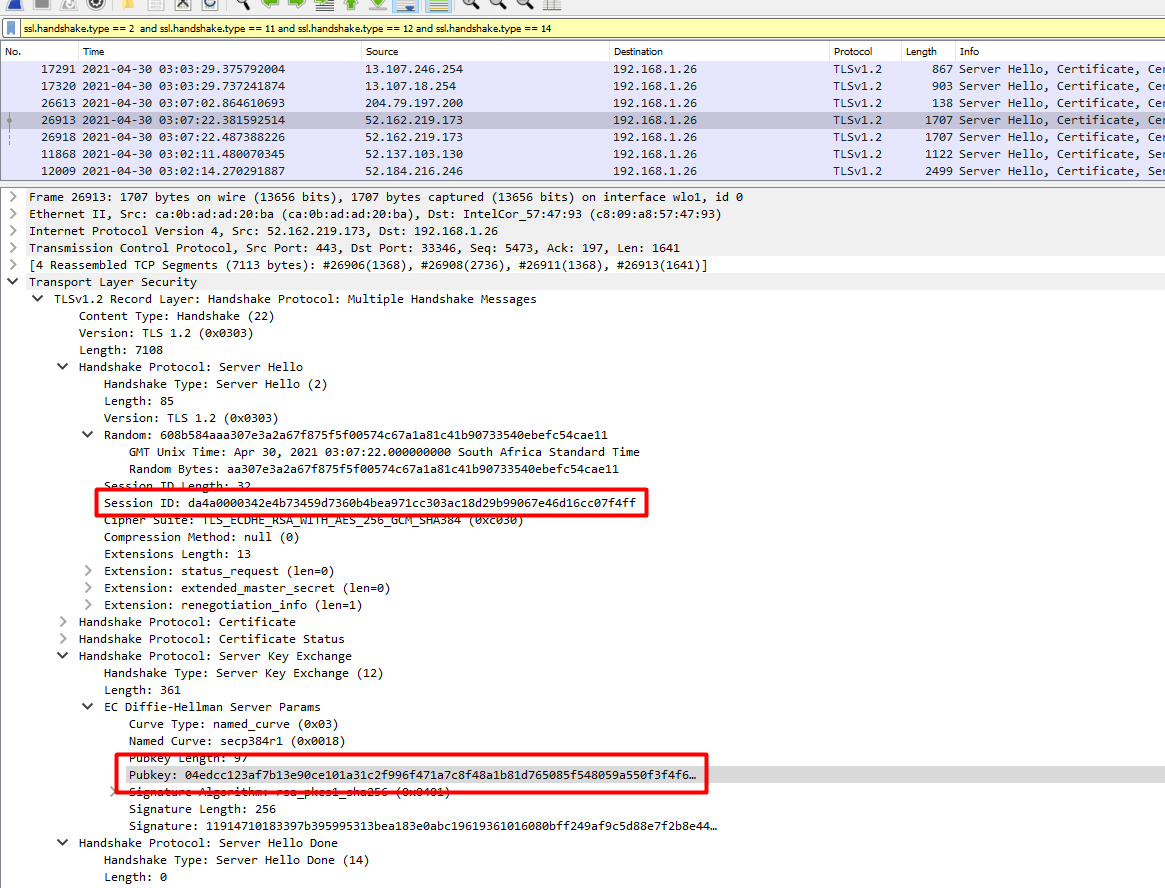
This one was tedious. Manually checking for this took a while but I found it eventually!
I found the following useful site with a filter list for TLS.
Wireshark Filter for SSL Traffic
In my search bar I had the following:
1
ssl.handshake.type == 2 and ssl.handshake.type == 11 and ssl.handshake.type == 12 and ssl.handshake.type == 14
I manually had to check the for the TLS session and find the answer but that query made our search criteria smaller.
9) Registered country
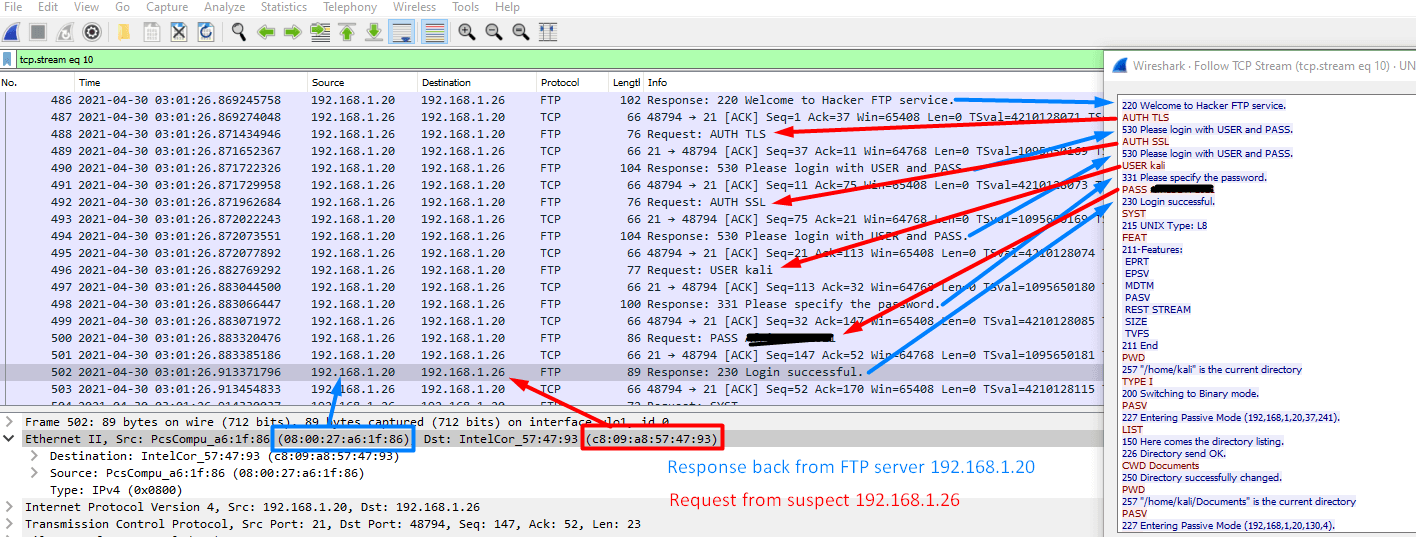
Here we need to get the MAC address of the FTP server and for this we need to search for ftp traffic.
In this case, we can see 192.168.1.26 is communicating to the FTP server and is showing as 192.168.1.20.
We just need to get the MAC address as below.
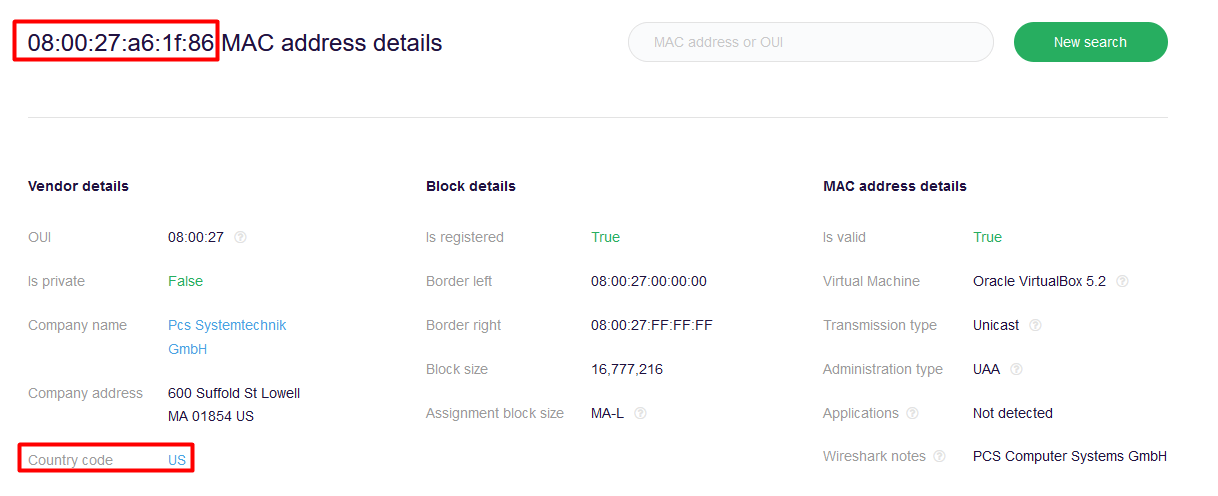
We can go to the following website to check the MAC address.
macaddress.io
Just a break down of how the packet flow works.
I got the first packet where this request started.
Bare with me.
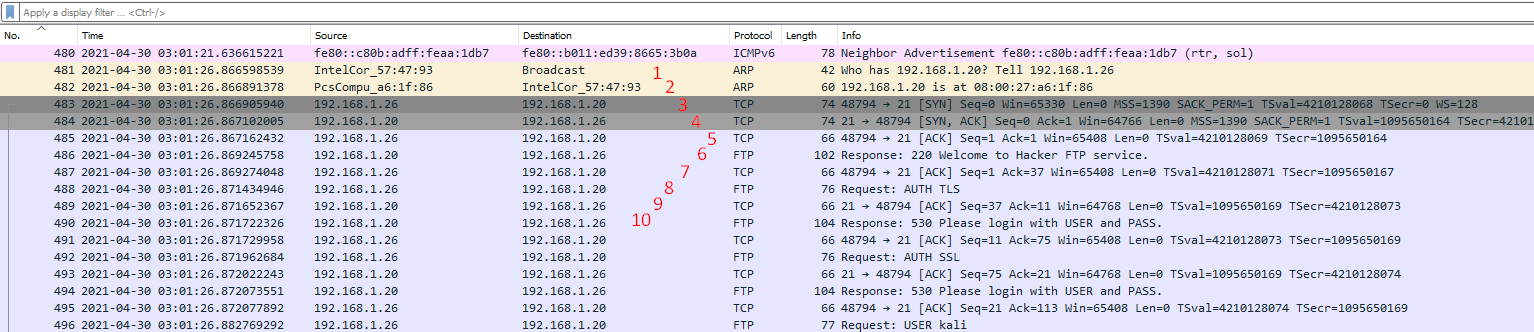
- IntelCor_57:47:93 is broadcasting an ARP asking who has 192.168.1.20
- PcsCompu_a6:1f:86 tells IntelCor_57:47:93 that it is 192.168.1.20
- 192.168.1.26 is now making a SYN connect on port 21 to 192.168.1.20
- 192.168.1.20 respondes with a SYN, ACK response back to 192.168.1.26
- 192.168.1.26 sends back an ACK to say it received 192.168.1.20 SYN,ACK
- 192.168.1.20 response with a Welcome message to 192.168.1.26
- 192.168.1.26 sends an ACK to say it got the Welcome message from 192.168.1.20
- 192.168.1.26 sends an AUTH TLS request to 192.168.1.20
- 192.168.1.20 sends an ACK to 192.168.1.26 to say they received it.
- 192.168.1.20 sends a Please login response to 192.168.1.26
So from this conversation, It shows that 192.168.1.26 is the suspect and 192.168.1.20 is the FTP Server.
192.168.26 is making a SYN connect on port 21 to 192.168.1.20 so 192.18.1.20 is the FTP server with the MAC address of 08:00:27:a6:1f:86
10) Suspicious folders
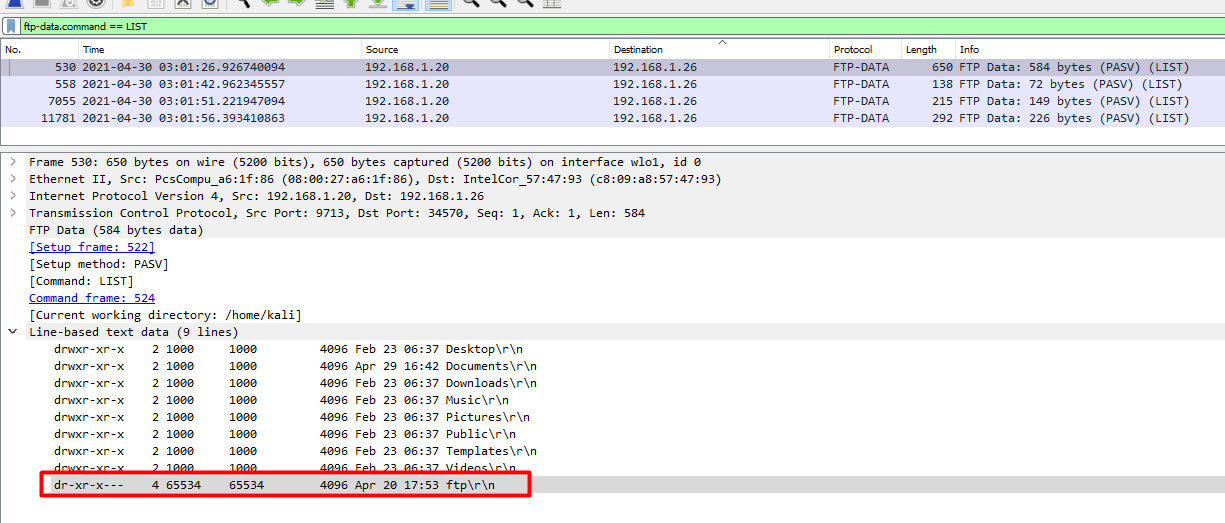
When we do a directory listing, a FTP server uses the LIST command.
With this in mind we can now do a search to get all requests for directory listing.
1
ftp-data.command == LIST
Here we find the directory and the time it was created.
11) Hidden files
Here we go to the packet ID 25639 by going to the toolbar, selecting Go and then Go to Packet or just pressing ctrl+g.
In the search to the right we enter the packet ID.
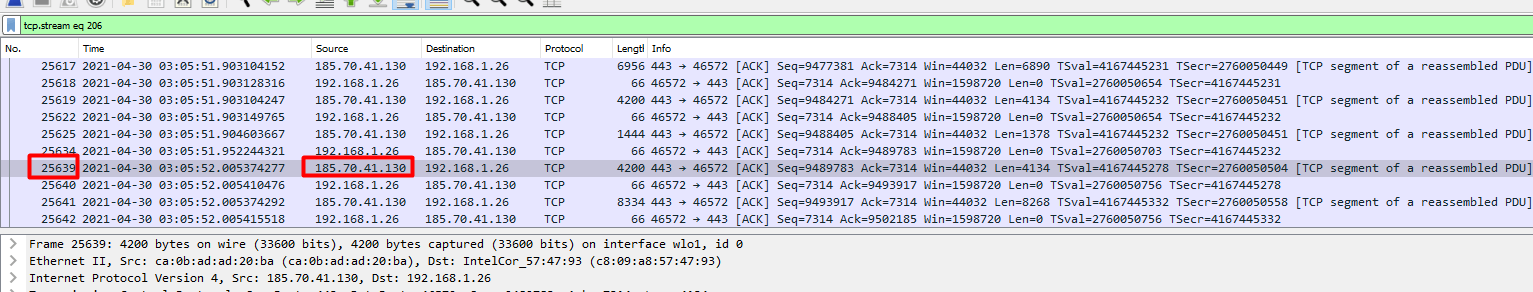
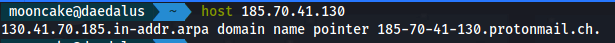
We see the IP address of 185.70.41.130.
When we do a reverse DNS lookup we get the following.
Domain name is from protomali.ch
We can right click on that packet and go to Follow and then select TCP stream.
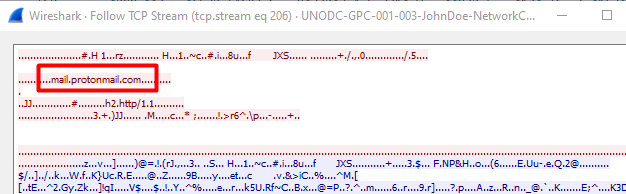
Here we see the domain mail.protomail.com
So we clearly looking for something that was downloaded from protomail
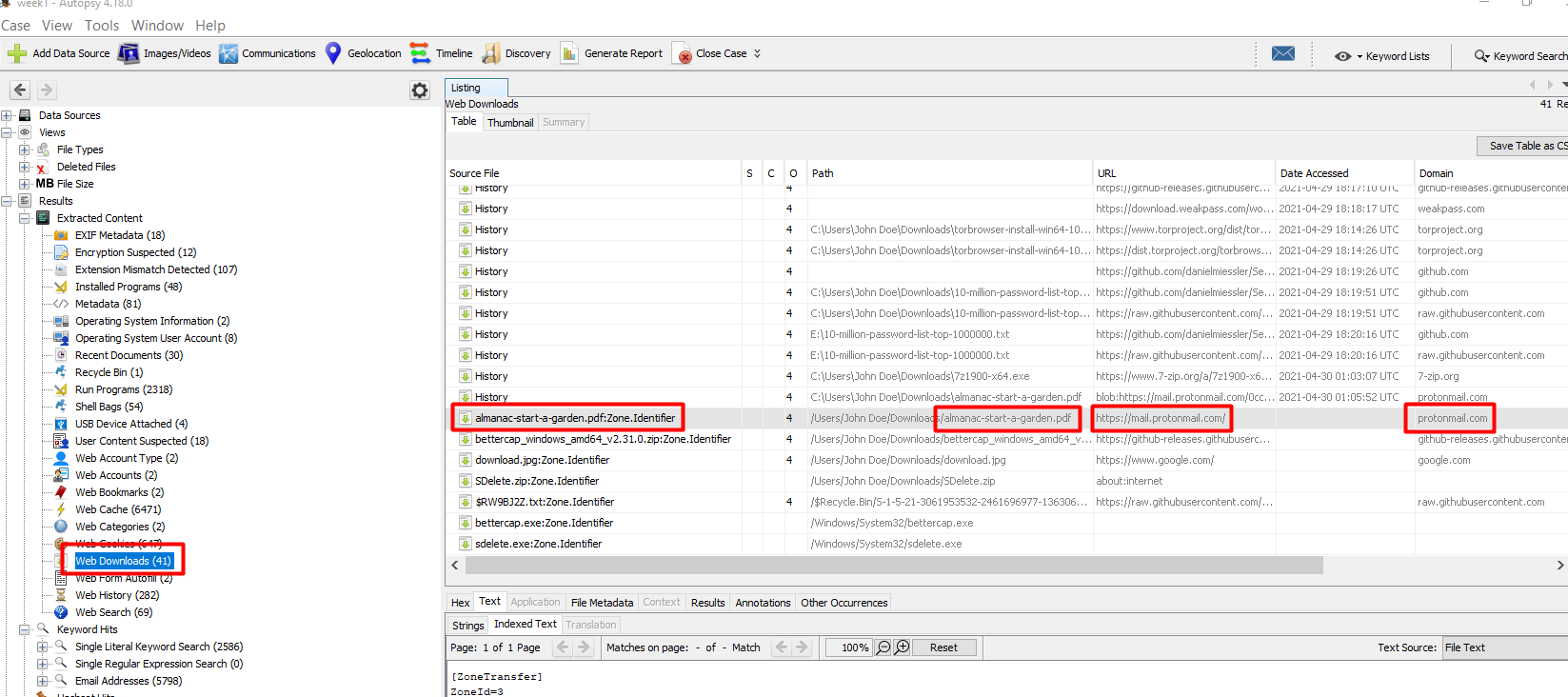
For the next part, we need to go back to Autopsy
We go to Web Downloads and we look for the protomail.com domain and then we see what file was downloaded.
12) TLS Domain
Here we go to the packet ID 27300 by going to the toolbar, selecting Go and then Go to Packet or just pressing ctrl+g.
In the search to the right we enter the packet ID.
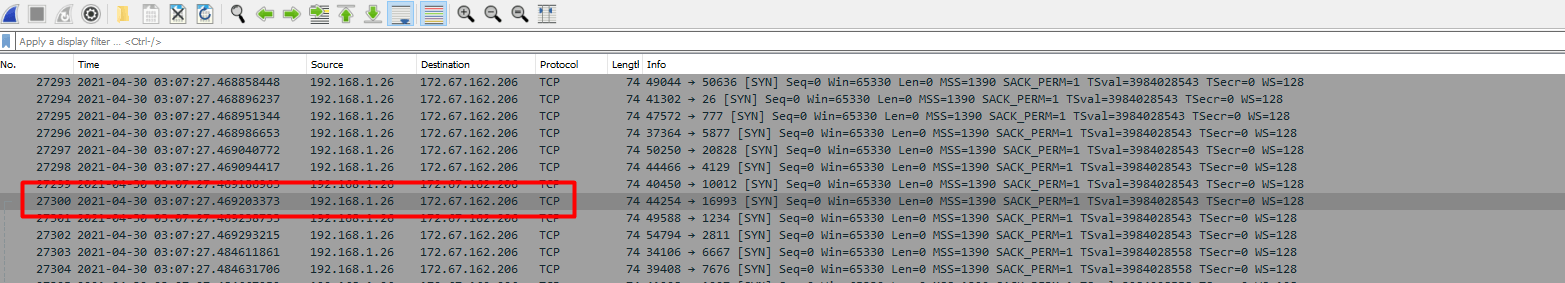
We find the IP 172.67.162.206.
Looking at the TCP stream we see that the IP is behind Cloudflare.
Doing a reverse DNS lookup didn’t bring back anything either.
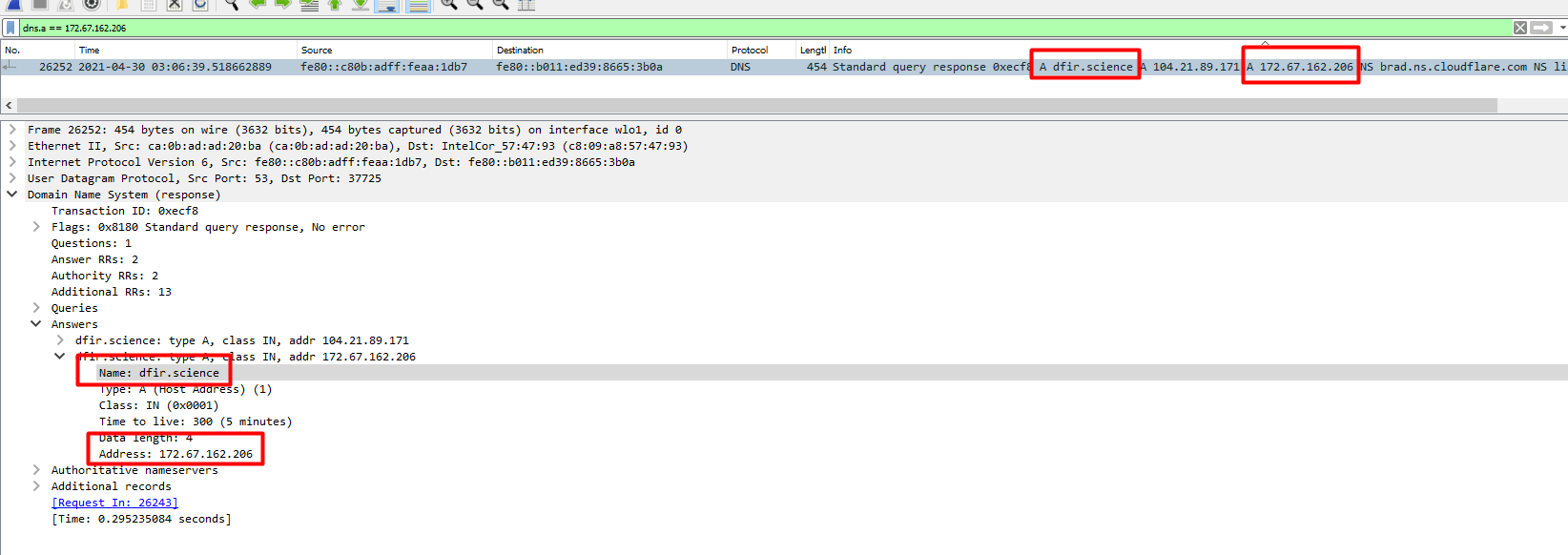
Let’s dig a bit deeper into the PCAP file.
We can use a search query to get this answer.
1
dns.a == 172.67.162.206
13) BTC Account
This challenge was by far the hardest of all the challenges.
It took me a week and a half to complete this challenge.
We had to find a Bitcoin account number.
That was it.
No, hints, no nothing.
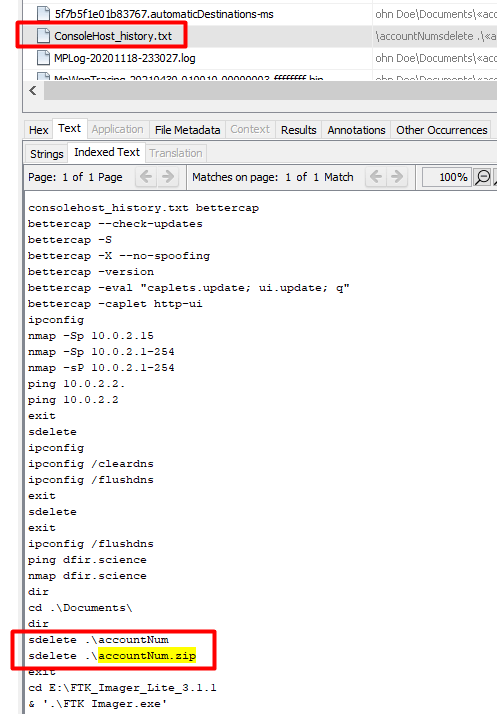
From previous questions and enumerations there was a certain filename called accountNum.zip that I saw on the suspect disk that was downloaded from the FTP server.
We had a problem though. The file was deleted off the suspect disk.
We saw this when we looked at the powershell ConsoleHost_history.txt previously
We would now have to look at this PCAP file to get this data out.
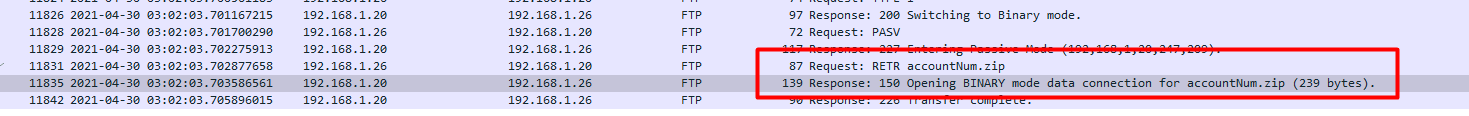
As we can see, the data was downloaded and it was 229 bytes but when we right click and follow the stream we don’t see the data.
Let’s take a closer look
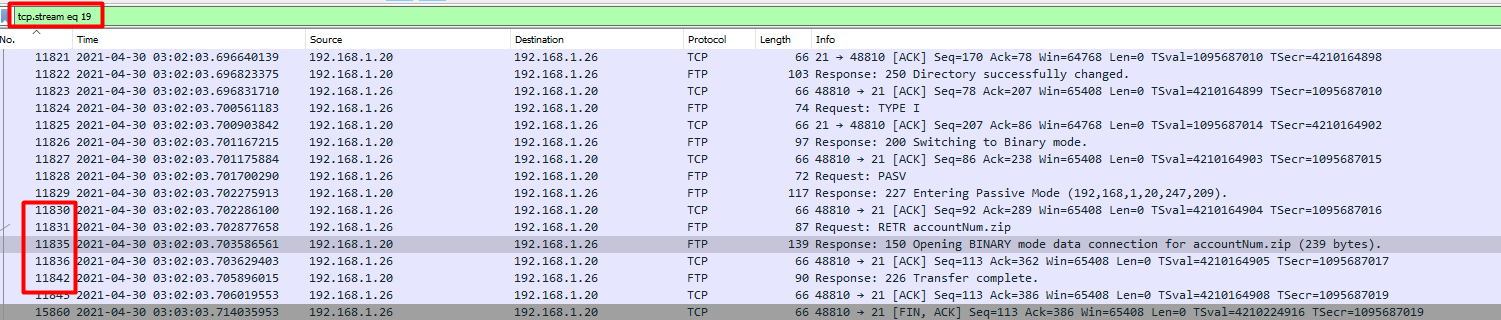
We are currently in tcp stream 19. If you look on the left, there are some packets missing between 11836 and 11842.
Let us check the next tcp stream after 19, 20.
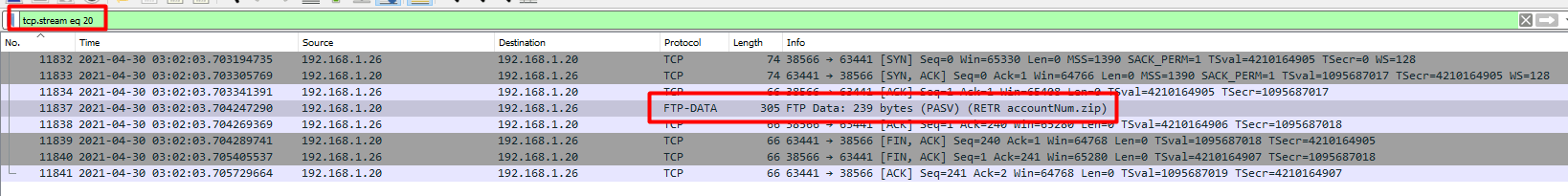
We could also just search for ftp-data
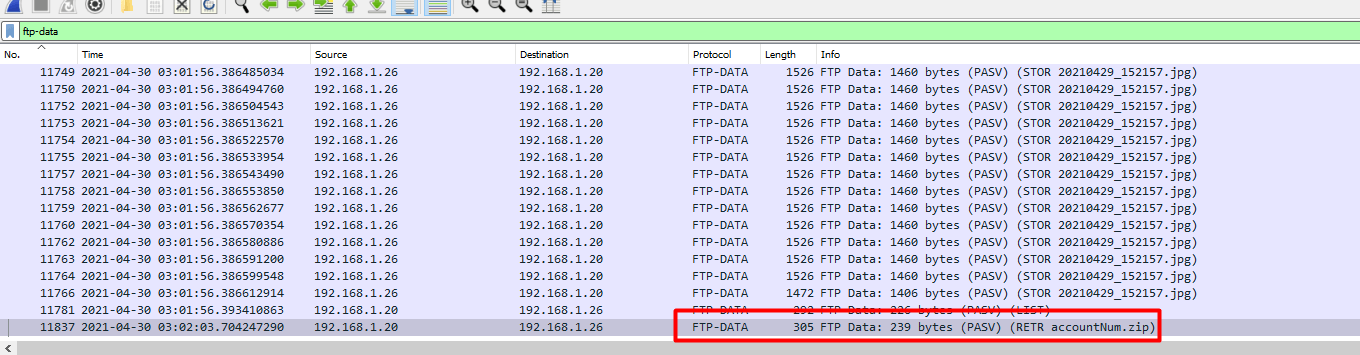
We can right click packet 11837 and follow the tcp stream.
We now can save this data as a raw format. Same method we did in the previous challenge for the 202104_29_152157.jpg file.
Make sure to save it as accountNum.zip
I tried to unzip the file but needless to say, it asked for a password.
I copied the zip file to my Kali machine so we can crack this password.
For this next step we needed to use zip2john to get a hash.
1
/usr/sbin/zip2john accountNum.zip > accountNum.hash
We now had to clean the hash so hashcat can understand it.
1
2
$ cat accountNum.hash
$zip2$*0*1*0*ee15e8c7b119a263*b778*2b*1cc963b2a5bee8ff04df77f9234157dfdb0f790a696feee642c9c246880769d8a82ca85690cb3f3b27e93f*90fa573c01d71c5971c1*$/zip2$
Looking at hashcat examples again, we can see that it is a WinZip format and we need to use the mode 13600.

Now this is where it got tricky. Bear in mind, these takes ages to finish so I spent days on end waiting.
I ran it against rockyou.txt NOTHING
Ran it against weakpass_2a NOTHING
I ran it with OneRuleToRuleThemAll.rule and rockyou.txt. NOTHING
I ran it with ?a?a?a?a?a?a?a NOTHING
I then started expirementing with variations of previous passwords.
We had found from previous, ctf2021, AFR1CA! and AfricaCTF2021
I started taking those password and doing lowercase, uppercase, reversing and doing all sorts of stuff. NOTHING
I took a full day break from this challenge.
I had to rethink this. This was when I saw a hint saying what the structure could be but still did not give me an idea how long the password would be.
The first method I tried was to bruteforce it with the following.
Thanks to Neonpegasus for your GPU!
1
hashcat -m 13600 -a 3 accountNum.hash ?u?a?a?a?a?l?l!
The second method I did while waiting for the above was a bit more behind my method of attacking it.
I thought about this logically as a typical user and thought, what do we as humans do with passwords? We repeat passwords but just add or change a certain aspect of it. e.g Rover21April –> Rover21May
What if I used the same thinking to this challenge? Break down the passwords seen into smaller chunks, and from the hints given, prepend or append them to a dictionary?
e.g Afr1can AfricanCTF2021 ctf2021 to Afr1can African CTF 2021 ctf
So I did some reading and I found how to prepend and append these to another wordlist. Now before I embarrass myself, the method I used does work, to a certain degree, BUT because it worked, I completely missed another attack mode, this is explained towards the end, that hashcat has to make this much simpler…but so we learn.
Anyway, so I created a rules file to prepend them to rockyou.txt.
My rules file looked like this:
1
2
3
4
5
^n^a^c^1^r^f^A
^n^a^c^i^r^f^A
^f^t^c
^F^T^C
^1^2^0^2
It may look weird but this is how prepend works in hashcat. The char ^ is the prepend function.
Say there is a word, dog, in the rockyou.txt file. You want to prepend the word cat to it. Your rule would look like ^t^a^c. So from left to right, hashcat will start with ^t and prepend it to dog making it tdog. The next one would be ^a and prepend that to tdog making it atdog. ^c prepends to atdog making it catdog. Done.
Append works the other way. You have the word dog and you want to append cat to it. Your rule would be ^c^a^t, thus ^c appends to dog making it dogc, ^a appends to dogc making it dogca and finally ^t appends to dogca making it dogcat. Simple.
So to use your rule file against a dictionary you would use the following:
1
hashcat -m 1000 -a 0 accountNum.hash -r rule.file rockyou.txt
So what I did was prepend the rules to rockyou.txt
1
2
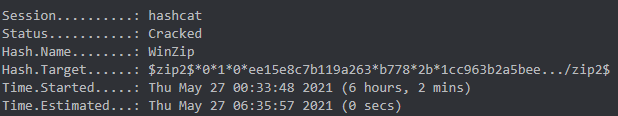
Time.Estimated...: (56 mins, 9 secs)
Status...........: Cracked
The easier way was to use the combinator attack.
Wait what, how did I miss that.
So essentially I could have just put those words in a file and run:
1
hashcat -m 13600 -a 1 accountNum.hash words.file rockyou.txt
Conclusion
This was by far the most challenging week and definitly questioned my sanity again!
STAY TUNED FOR WEEK 4 WRITE UP SOON!