Week 2
We were given a RAM Acquisition of the suspect disk for week 2.
A RAM Acquisition is just a procedure of copying the contents of volatile memory to non-volatile storage.
I have done a few RAM disk analysis in the past and I knew immediatly to get an application called Volatility but this one got me stumped for an hour or so due to the fact that I downloaded Volatility 2 and I just could not get the RAM disk to work. After some reading I managed to figure out I needed to get Volatility 3.
I found out that it might be because of the new Windows versions that Volatility 2 doesn’t support or just something specific with this dump created.
The differece between Volatility 2 and 3 quite big due to the fact that 3 is lacking in a lot of the commands that 2 has so some of these questions you really had to come up with alternative methods to solve.
Some resources I used:
We again were given 11 challenge questions to do.
1) Be Brave
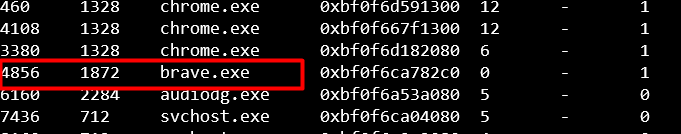
This one was straight foward. In Volatility we have the plugin called windows.pslist which lists all the processes.
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.pslist
2) Image Verification
We can run the following command to get the SHA256 hash value.
1
CertUtil -hashfile ../20210430-Win10Home-20H2-64bit-memdump.mem sha256
3) Let’s Connect
With this one we can use another plugin for Volatility called windows.netstat
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.netstat | findstr ESTABLISHED
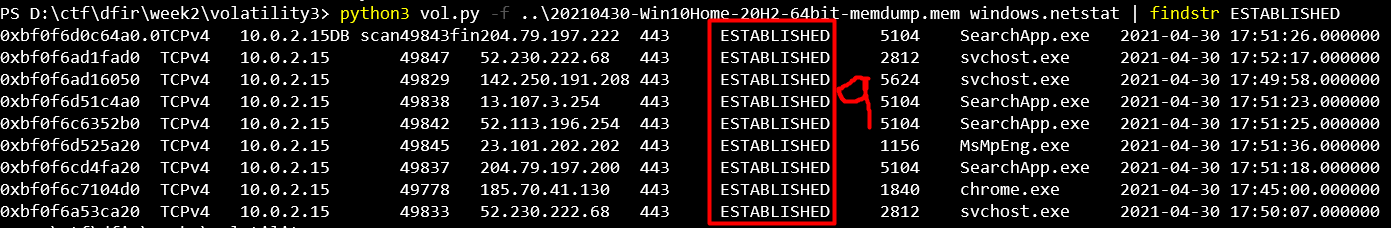
I counted.
I entered my answer, WRONG!
I recounted, same result.
I was confused.
I reran the command multiple times and got the same outcome.
Was I doing something wrong?
After while I decided to copy the memory dump to my Kali machine and see if I get the same result.
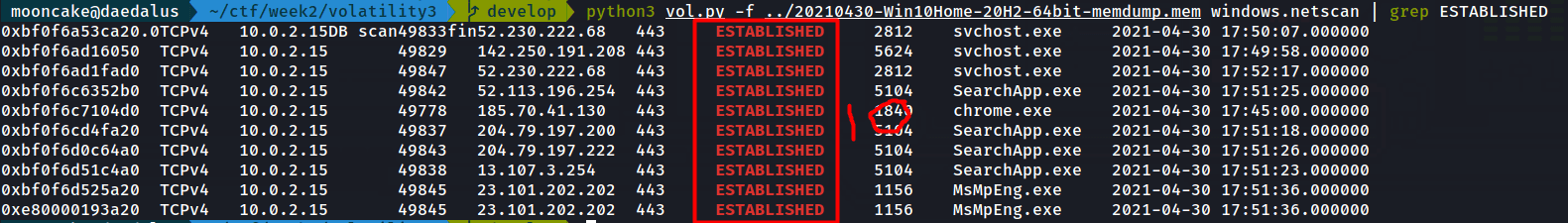
Wait what? A different outcome?
Now if you are thinking, it’s because I had a different version of Volatility then you are wrong. It’s was same cloned version from Volatility3
Maybe it’s a windows thing? I cannot explain this. Did anyone experience the same?
At this point I just decided to rather do the rest of the challenges of week2 on my Kali machine.
I just couldn’t trust Volatility on windows.
4) RAM Acquisition Time
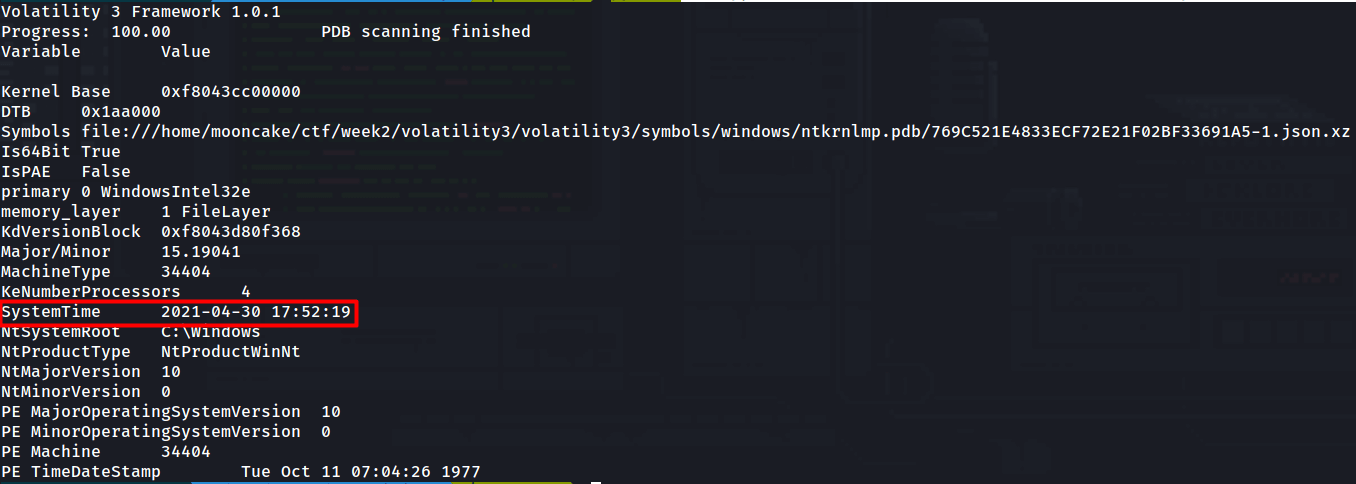
This one was fairly easy and we just had to run the following Volatility plugin.
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.info
5) Chrome Connection
This one is pretty straight forward.
From previous question we see a list of established connections and one of them is chrome.exe
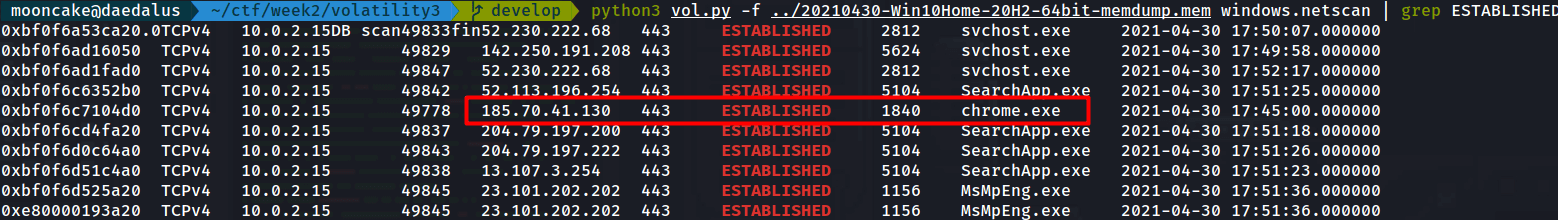
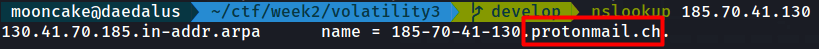
We see that it is connected to a destination IP. We now need to find the domain name.
Let us do a reverse lookup on the destination IP.
6) Hash Hash Baby
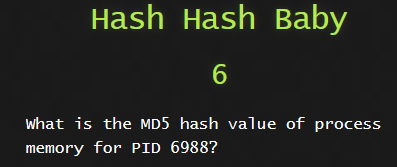
Here we have to dump the process PID 6988 with a plugin called pslist.
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.pslist --pid 6988 --dump
A file gets dumped into the folder and then all we have to do is get the MD5 hash value.
1
md5sum pid.6988.0x1c0000.dmp
7) Offset Select
This one had me stumped for pretty much a few hours.
Getting the offset is easy.
I had the right command.
The problem came in with a typo when the question first came out.
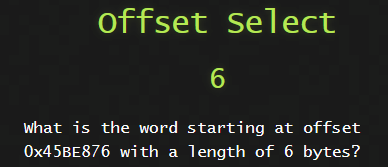
The original offset was wrong.
This was the original question. The offset here was 0x45BE87B
Now when I used that offset
1
hexdump -s 0x45BE87B -C ../20210430-Win10Home-20H2-64bit-memdump.mem | more
I would get the following result.
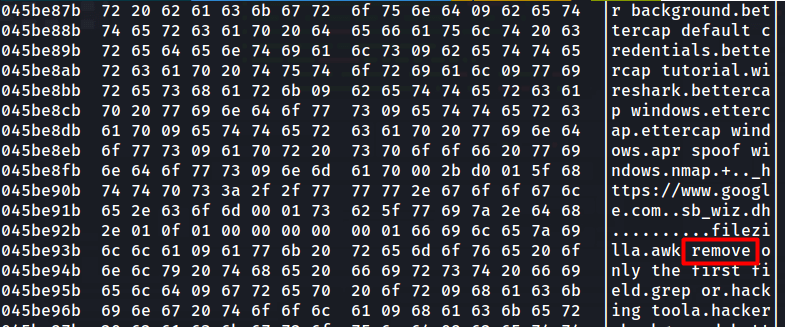
There was no word with a length of 6 bytes on that offset and the only one that was closest was at offset 0x45be93b with the word removed.
This had me question my sanity and ability of using hexdump to find offsets and I went down a path that I will not talk about. Googling down rabbit holes. haha.
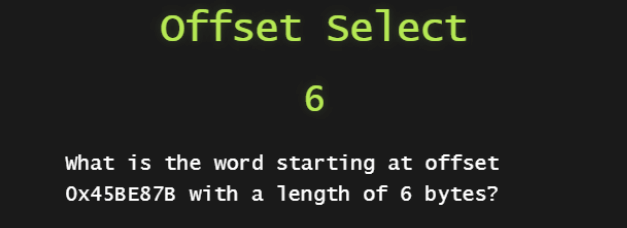
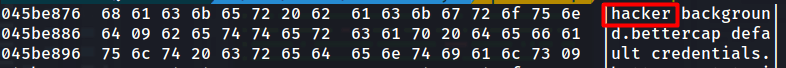
THANKFULLY I noticed sometime later that the offset was changed in the question and when I checked the offset again, this time 0x45BE876, I got the correct answer.
Thanks DFIRScience for thinking I was going insane! :-)
1
hexdump -s 0x45BE876 -C ../20210430-Win10Home-20H2-64bit-memdump.mem | more
8) Process Parents Please
For this one we will just use windows.pslist
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.pslist
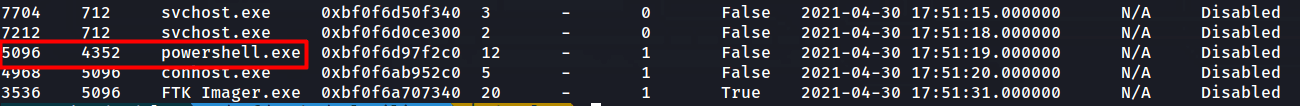
We have a look at the process powershell.exe and see it has a PPID of 4352.
A PID is a Process ID that each process has on the system. In this case, poweshell.exe has a PID of 5096.
A PPID is a Parent Process ID. Each process is assigned a PPID and this tells us which process started it. In this case, the PPID of powershell.exe is 4352.
We now have to find this PPID 4352 and this will tell us the parent process of powershell.exe

Now we have the time the parent process was created.
9 Finding Filenames
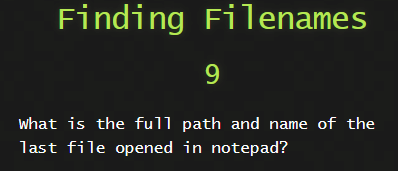
For this one we are going to use the windows.cmdline plugin.
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.cmdline | grep notepad
10) Hocus Focus
This one we use the plugin windows.registry.userassist
1
python3 vol.py -f ../20210430-Win10Home-20H2-64bit-memdump.mem windows.registry.userassist | grep Brave
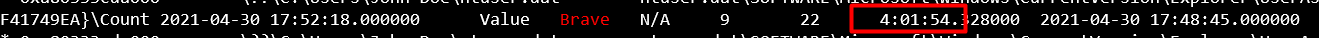
11) Meetings
This one for me was the hardest for week 3.
There was no indication where to even begin or look for this answer.
I searched every nook and cranny on the RAM and Disk Image.
That date did not exist anywhere in a search or timeline.
I was stumped.
Without the hint for the week, I would have struggled to even find it.
To be honest. I had the file open in week 1 and I didn’t read the whole thing, only some parts. If I read every page, I would have seen it!
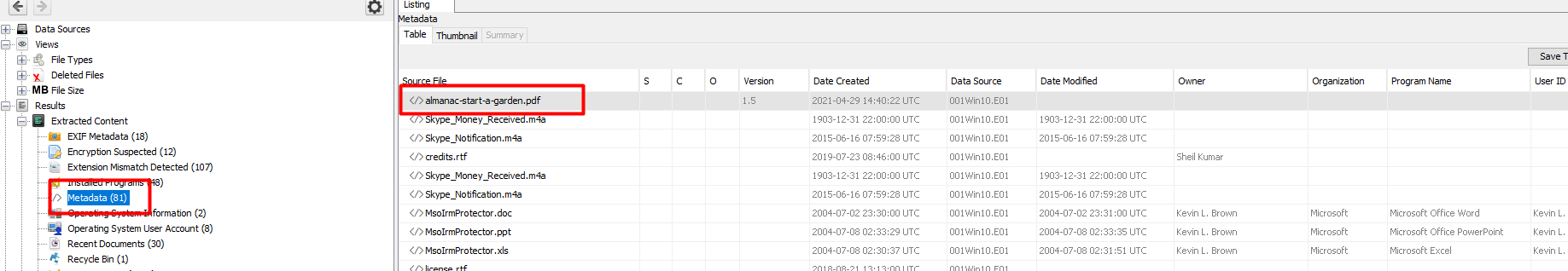
For this we need to open Autopsy.
With the hint from the week I knew exactly where to look.
On the left we click Metadata then we right click almanac-start-a-garden.pdf and extract it to our local machine.
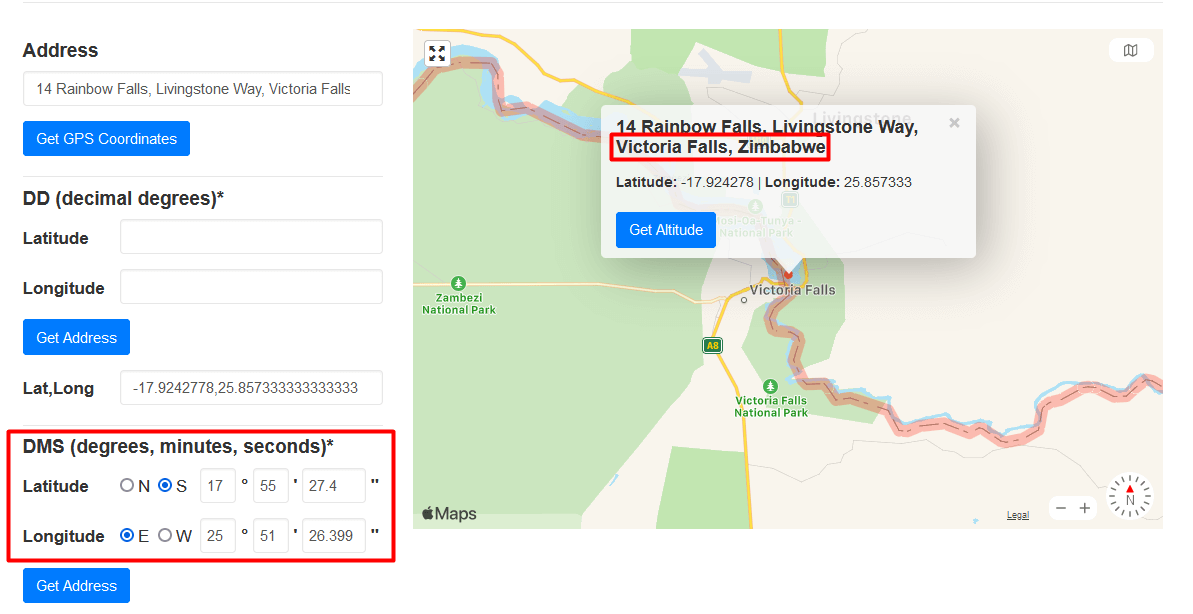
Open the PDF and scroll to page 11.
You will find some GPS coordanates with the date 2021-06-13 at the bottom of that page.

Let’s go to the website we went to in week 1 https://www.gps-coordinates.net/
We enter the GPS co-ordinates and then we find the place and country.
I have never been to Victoria Falls.
Conclusion
All in all it was a fun week, apart from those 3 challenges that gave me hassels but in the end I solved them.
Stay tuned for week 3 write up in the next few days